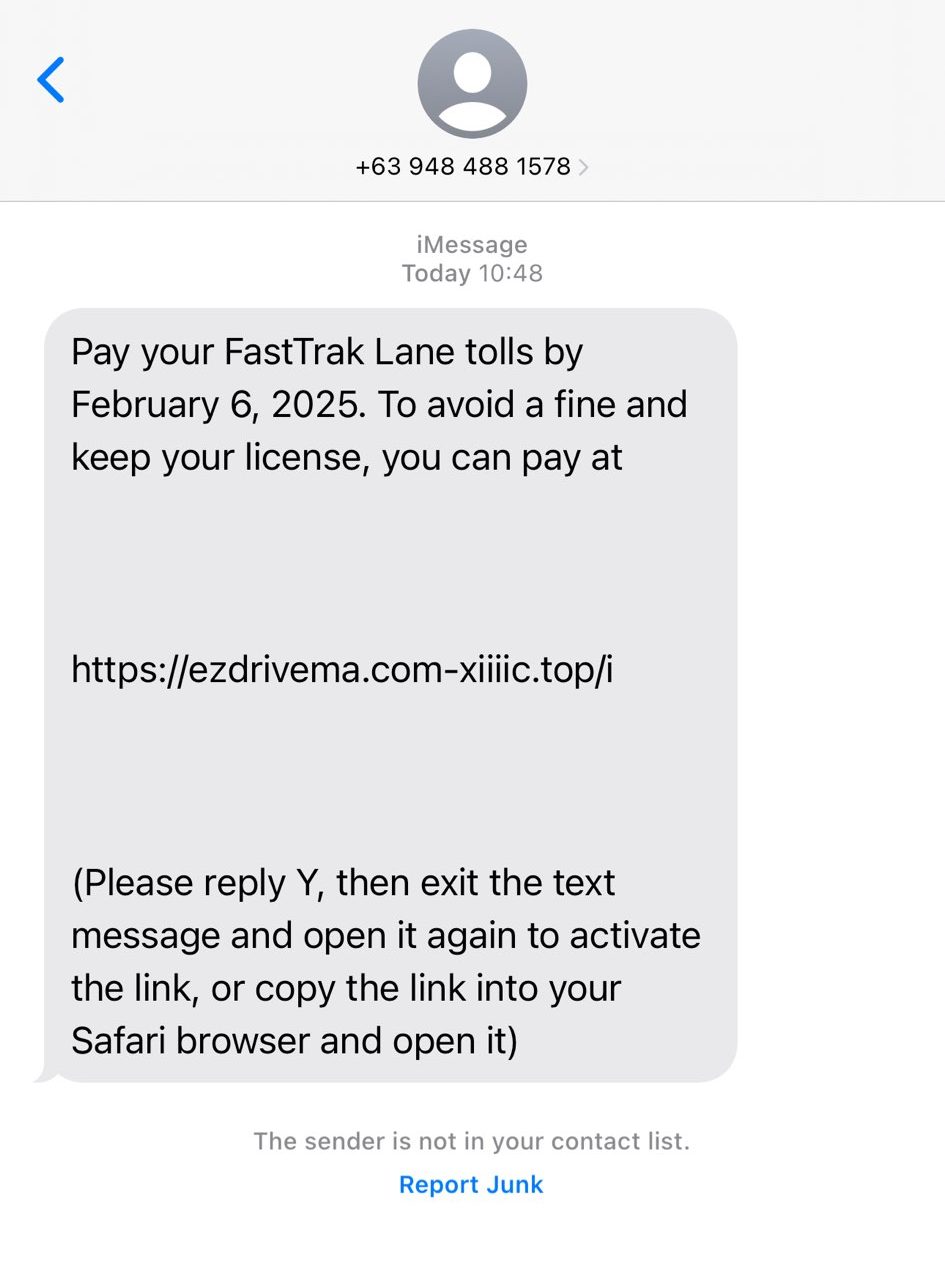
Most days I ignore, delete, and/or block phishing emails or smishing messages. However, let’s dig into one to see what we can find.
Phone Number
A quick Google search shows that +63 is a Philippines country code. Hopefully this is an immediate signal that it is a phishing attempt.
No results for the full phone number shows up anymore. Honestly, it’s probably a throw-away number.
URL Analysis
I put the URL into URLScan: https://urlscan.io/result/e478ca5f-d6f8-424b-b25f-afab8cc38236/
Results show no redirections but straight to a landing page for the ezdrivema[.]com-siiiic[.]top domain.
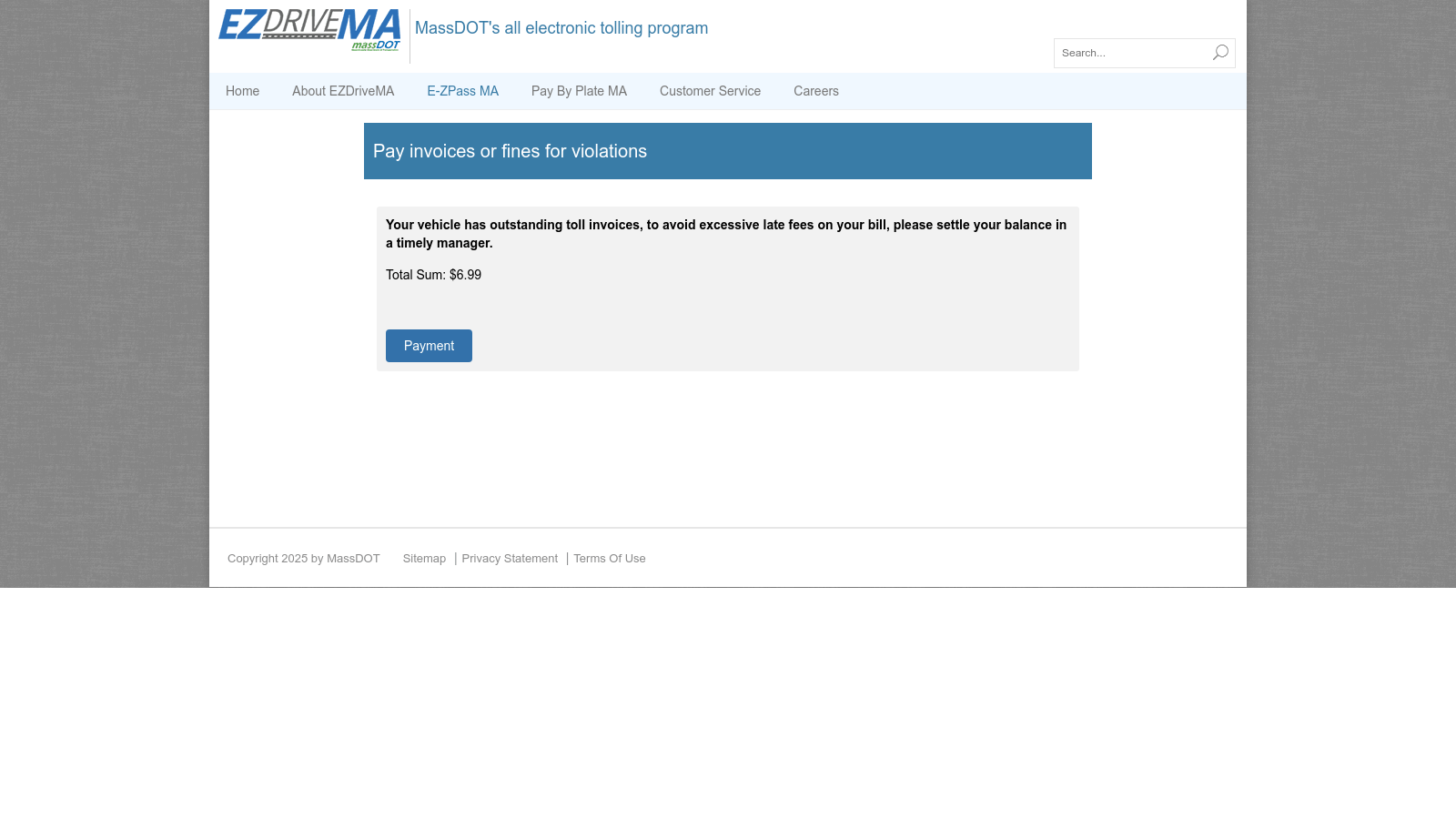
We can see the page is a clone of the Massachusetts’ Department of Transportation EZPass program: https://www.mass.gov/ezdrivema. Funny enough, their website is alerting against this smishing attack:
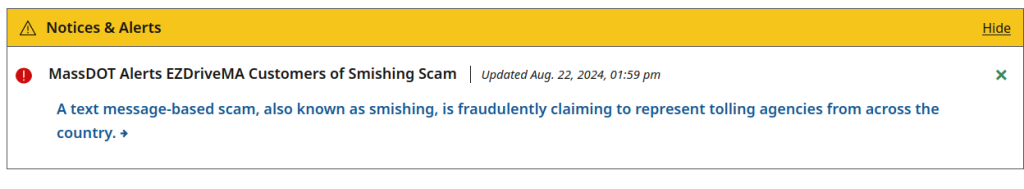
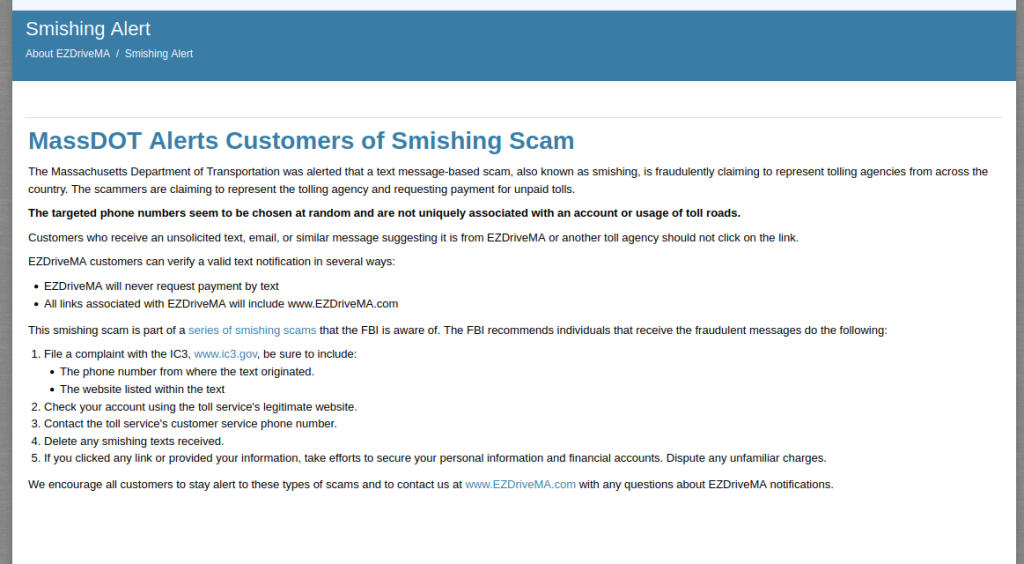
The URLScan result shows a POST form /ezpassmalogin that is associated with the whole page whenever the user clicks on the button. However, all other links on the page lead to the legitimate MA DOT page. I’m not sure what all the javascript is doing, but it looks like it could be a “man in the middle” type scenario.
I also tried to access the URL via AnyRun, but it could not reach it.
VIrusTotal results are below:
0/94, https://www.virustotal.com/gui/domain/ezdrivema.com-xiiiic.top
5/96, https://www.virustotal.com/gui/url/28782f6b4692ca68adc1cc37ca2182ddcc10ad48fb3237aed1494b951bd1094b
Looks like even VirusTotal returns a 404 error. I think the URLScan results are cached from when a different user scanned it before the attacker took down the domain.
The domain was served by 47.89.248[.]140. This is a domestic geolocated IP address and owned by Alibaba cloud services. NSlookup shows that the IP serves also the following domains:
ezdrivema[.]com-xiiiic[.]top
ezdrivema[.]com-xiiiir[.]top
ezdrivema[.]com-xiiiij[.]top
ezdrivema[.]com-heeeq[.]top
ezdrivema[.]com-xiiiif[.]top
ezdrivema[.]com-xiiiia[.]top
ezdrivema[.]com-heeet[.]top
ezdrivema[.]com-xiiiin[.]top
ezdrivema[.]com-heeec[.]top
ezdrivema[.]com-xiiiiq[.]top
ezdrivema[.]com-xiiiik[.]top
ezdrivema[.]com-xiiiib[.]top
ezdrivema[.]com-heeez[.]top
ezdrivema[.]com-heeef[.]top
ezdrivema[.]com-youshz[.]top
ezdrivema[.]com-gdsgdff[.]top
ezdrivema[.]com-youshc[.]top
ezdrivema[.]com-guonix[.]top
ezdrivema[.]com-youshs[.]top
ezdrivema[.]com-gdsgdfa[.]top
ezdrivema[.]com-gdsgdfd[.]top
ezdrivema[.]com-guonib[.]top
ezdrivema[.]com-youshe[.]top
ezdrivema[.]com-gdsgdfz[.]top
ezdrivema[.]com-guonia[.]top
ezdrivema[.]com-guonis[.]top
ezdrivema[.]com-gdsgdfr[.]top
ezdrivema[.]com-youshq[.]top
ezdrivema[.]com-guonif[.]top
ezdrivema[.]com-guonit[.]top
ezdrivema[.]com-gdsgdfq[.]top
ezdrivema[.]com-gdsgdfe[.]top
ezdrivema[.]com-guoniz[.]top
ezdrivema[.]com-youshx[.]top
ezdrivema[.]com-guonih[.]top
ezdrivema[.]com-gdsgdfc[.]top
Looks like the scammers are varying the parent domain pattern. This IP address also has a pattern of phishing websites before 2023. However, all of them also seem to be HTTP status 404.
Conclusion
I have a virtual sms number to be used for testing smishing attackers, but I’m not ready to pay for international texts.
And all the domains are already down by the attacker.