This is more or less a part two to the naprava.exe analysis. Turns out the SD card holds many malicious surprises.
Again, this is a 14-year-old malware executable from Moldova that was inadvertently stored on a SD card.
Analysis
shakira.exe loads the following dlls in chronological order:
- +46ms
- ntdll.dll
- kernel32.dll
- +62 ms
- KernelBase.dll
- user32.dll
- gdi32.dll
- lpk.dll
- usp10.dll
- msvcrt.dll
- +78 ms
- C:\Windows\winsxs\x86_microsoft.windows.common-controls_6595b64144ccf1df_5.82.7601.18837_none_ec86b8d6858ec0bc\comctl32.dll
- advapi32.dll
- sechost.dll
- rpcrt4.dll
- loeaut32.dll
- ole32.dll
- shell32.dll
- shlwapi.dll
- imm32.dll
- msctf.dll
- +203 ms
- apphelp.dll
- +218 ms
- svchost.exe
The executable runs process svchost.exe. The process drops another executable: C:\Users\admin\xuat.exe. Then xuat.exe writes to the registry key HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon with the value explorer.exe,C:\Users\admin\xuat.exe and named Shell. The dropper did this in order to keep persistence at restart and logon. The process then reads many various registry entries regarding network connections.
At +906 ms the process creates a connection to 44.221.84[.]105:33111 (slade.safehousenumber[.]com). The process sends 21 bytes of data via UDP protocol:
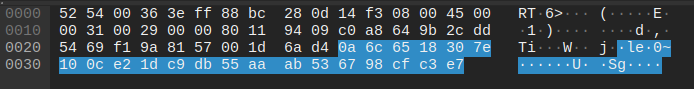
At +120 seconds, the xuat.exe process creates a connection to 193.166.255[.]171:33111 (portal.roomshowerbord[.]com). The process sends 21 bytes of data via UDP protocol.
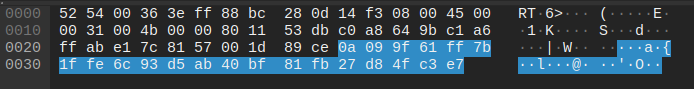
At +128 seconds, the Windows Media Player Network Sharing Service Configuration Application (C:\Program Files\Windows Media Player\wmpnscfg.exe)runs in the background and gathers client information (reads computer name, checks supported languages, and other sysinfo).
At +151 seconds, the xuat.exe process creates a connection to 44.221.84[.]105:33111 (slade.safehousenumber[.]com). The process sends 21 bytes of data via UDP protocol:
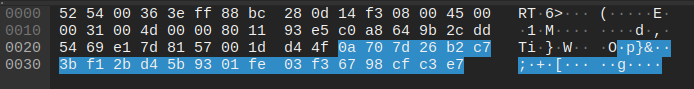
The malware seems to gather system information and send it to C2 servers.
Ghidra produced the following decompiled output:
void entry(void)
{
undefined4 *puVar1;
undefined4 extraout_ECX;
uint extraout_EDX;
byte *pbVar2;
char **local_74;
_startupinfo local_70;
int local_6c;
char **local_68;
int local_64;
_STARTUPINFOA local_60;
undefined *local_1c;
void *pvStack_14;
undefined *puStack_10;
undefined *puStack_c;
undefined4 local_8;
puStack_c = &DAT_00412058;
puStack_10 = &DAT_0041148c;
pvStack_14 = ExceptionList;
local_1c = &stack0xffffff6c;
local_8 = 0;
ExceptionList = &pvStack_14;
__set_app_type(2);
_DAT_00412038 = 0xffffffff;
_DAT_00412078 = 0xffffffff;
puVar1 = (undefined4 *)__p__fmode();
*puVar1 = DAT_0041214c;
puVar1 = (undefined4 *)__p__commode();
*puVar1 = DAT_0041206c;
_DAT_00412070 = *(undefined4 *)_adjust_fdiv_exref;
FUN_0041147b();
if (DAT_0041208c == 0) {
__setusermatherr(&DAT_00412254);
}
FUN_0041147b();
_initterm(&DAT_00412090,&DAT_00412090);
local_70.newmode = DAT_00412020;
__getmainargs(&local_64,&local_74,&local_68,DAT_00412080,&local_70);
_initterm(&DAT_00412090,&DAT_00412090);
pbVar2 = *(byte **)_acmdln_exref;
if (*pbVar2 != 0x22) {
do {
if (*pbVar2 < 0x21) goto LAB_0041140f;
pbVar2 = pbVar2 + 1;
} while( true );
}
do {
pbVar2 = pbVar2 + 1;
if (*pbVar2 == 0) break;
} while (*pbVar2 != 0x22);
if (*pbVar2 != 0x22) goto LAB_0041140f;
do {
pbVar2 = pbVar2 + 1;
LAB_0041140f:
} while ((*pbVar2 != 0) && (*pbVar2 < 0x21));
local_60.dwFlags = 0;
GetStartupInfoA(&local_60);
GetModuleHandleA((LPCSTR)0x0);
local_6c = FUN_004109ec(extraout_ECX,extraout_EDX);
/* WARNING: Subroutine does not return */
exit(local_6c);OSINT
shakira.exe
a94ccc4af328865384badd276d1f1a4bb38fa83edc006ad275b1f767eaf17c53
53/64, https://www.virustotal.com/gui/file/a94ccc4af328865384badd276d1f1a4bb38fa83edc006ad275b1f767eaf17c53
Associated with the Armadillo malware packer.
xuat.exe
a94ccc4af328865384badd276d1f1a4bb38fa83edc006ad275b1f767eaf17c53
Same as/Part of above file.
slade.safehousenumber[.]com
9/94, https://www.virustotal.com/gui/domain/slade.safehousenumber.com
GoDaddy registered domain known for phishing.
murik.portal-protection.net[.]ru
3/94, https://www.virustotal.com/gui/domain/murik.portal-protection.net.ru
Domain registered with Russian registrar RU-CENTER-RU. Known malware domain.
banana.cocolands[.]su
5/94, https://www.virustotal.com/gui/domain/banana.cocolands.su
Registered with NIC.ru domain registrar. Known malware domain.
portal.roomshowerbord[.]com
5/94, https://www.virustotal.com/gui/domain/portal.roomshowerbord.com
Domain registered with GoDaddy. Known malware domain.
44.221.84[.]105
1/94, https://www.virustotal.com/gui/ip-address/44.221.84.105/details
Supposedly an Amazon domestic IP. But associated with malware.
193.166.255[.]171
2/94, https://www.virustotal.com/gui/ip-address/193.166.255.171
Finnish IP serving phishing domains.
Conclusion
Definitely similar to naprava.exe. Maybe the same threat actor wrote this malware where I contracted it in the Chisinau, Moldova internet cafe.
Indicators of Compromise
| AnyRun Link | https://app.any.run/tasks/abdd8821-c4aa-4f97-9d86-4eb5f1983023 |
| File Path | ..\havesit\shakira.exe |
| File Name | shakira.exe |
| SHA256 | a94ccc4af328865384badd276d1f1a4bb38fa83edc006ad275b1f767eaf17c53 |
| C2 Domain | slade.safehousenumber[.]com |
| C2 Domain | murik.portal-protection.net[.]ru |
| C2 Domain | banana.cocolands[.]su |
| C2 Domain | portal.roomshowerbord[.]com |
| C2 IP | 44.221.84[.]105 |
| C2 IP | 193.166.255[.]171 |