This is more or less a part three to the naprava.exe analysis. Turns out the SD card holds many malicious surprises.
Again, this is a 14-year-old malware executable from Moldova that was inadvertently stored on a SD card.
Analysis
Submitted the file to AnyRun. The file performs the following actions (with the respective timestamps):
| +47ms | File drops C:\Users\admin\lzmjqt.exe |
| +63ms | lzmjqt.exe writes a new shell key to WinLogon registry |
| +218ms | Creates process svchost.exe |
| +281ms | svchost.exe runs file C:\Users\admin\lzmjqt.exe |
| +1313ms | DNS request to slade.safehousenumber[.]com |
| +31039ms | murik.portal-protection[.]net[.]ru |
| +60758ms | world.rickstudio[.]ru |
| +91480ms | banana.cocolands[.]su |
| +121s | DNS request to portal.roomshowerbord[.]com |
| +150s | DNS request to slade.safehousenumber[.]com |
| +271s | DNS request to portal.roomshowerbord[.]com |
The executable drops the lzmjqt.exe. This second executable writes a persistent reverse shell to the WinLogon registry. Then the original executable creates a svchost.exe process. The svchost.exe then runs the dropped file. This malware then reaches out to its C2 domains — slade.safehousenumber[.]com and portal.roomshowerbord[.]com.
AnyRun captured a pcap and the DNS output is such:
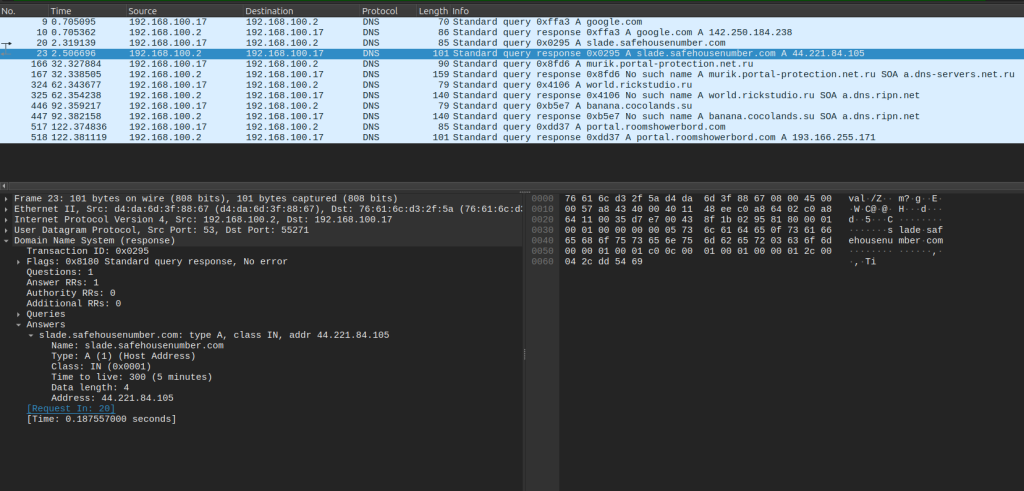
The first request sent to safehousenumber (44.221.84[.]105)received a response, containing the following bytes:
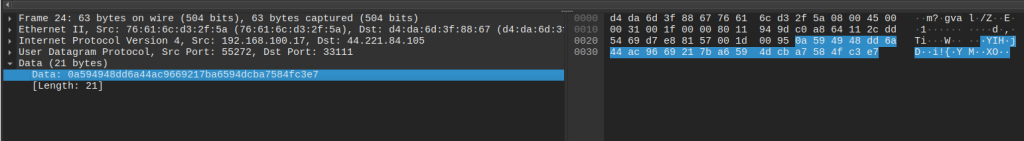
The second request is sent to portal.roomshowerbord[.]com (193.166.255[.]171) and the response is received, containing the following bytes:
Reverse engineering the malware with Ghidra gives the following decompilation:
void entry(void)
{
undefined4 *puVar1;
undefined4 extraout_ECX;
undefined4 extraout_EDX;
byte *pbVar2;
char **local_74;
_startupinfo local_70;
int local_6c;
char **local_68;
int local_64;
_STARTUPINFOA local_60;
undefined *local_1c;
void *pvStack_14;
undefined *puStack_10;
undefined *puStack_c;
undefined4 local_8;
puStack_c = &DAT_0040f058;
puStack_10 = &DAT_0040e0a8;
pvStack_14 = ExceptionList;
local_1c = &stack0xffffff74;
local_8 = 0;
ExceptionList = &pvStack_14;
__set_app_type(2);
_DAT_00411de8 = 0xffffffff;
_DAT_0040f030 = 0xffffffff;
puVar1 = (undefined4 *)__p__fmode();
*puVar1 = DAT_0040f040;
puVar1 = (undefined4 *)__p__commode();
*puVar1 = DAT_0040f020;
_DAT_00411ddc = *(undefined4 *)_adjust_fdiv_exref;
FUN_0040e07a();
if (DAT_00411de4 == 0) {
__setusermatherr(&DAT_004185c4);
}
FUN_0040e07a();
_initterm(&DAT_0040f03c,&DAT_0040f03c);
local_70.newmode = DAT_00411dd0;
__getmainargs(&local_64,&local_74,&local_68,DAT_00411de0,&local_70);
_initterm(&DAT_0040f03c,&DAT_0040f03c);
pbVar2 = *(byte **)_acmdln_exref;
if (*pbVar2 != 0x22) {
do {
if (*pbVar2 < 0x21) goto LAB_0040e01b;
pbVar2 = pbVar2 + 1;
} while( true );
}
do {
pbVar2 = pbVar2 + 1;
if (*pbVar2 == 0) break;
} while (*pbVar2 != 0x22);
if (*pbVar2 != 0x22) goto LAB_0040e01b;
do {
pbVar2 = pbVar2 + 1;
LAB_0040e01b:
} while ((*pbVar2 != 0) && (*pbVar2 < 0x21));
local_60.dwFlags = 0;
GetStartupInfoA(&local_60);
GetModuleHandleA((LPCSTR)0x0);
local_6c = FUN_0040dee8(extraout_ECX,extraout_EDX);
/* WARNING: Subroutine does not return */
exit(local_6c);
}This executable function is the runtime startup routine that:
- Sets up exception handling.
- Configures the application type as a console app.
- Initializes global variables (e.g., file mode, floating-point settings).
- Runs initializers (e.g., C++ constructors) via _initterm.
- Retrieves and parses command-line arguments.
- Gathers startup information.
- Calls the user-defined main function (FUN_0040dee8).
- Exits with main’s return value.
We would need the dropped binary to see what the real malware does.
OSINT
| Filename | 7zsfx.exe |
| VirusTotal Score | 18/43 |
| MD5 | 3aeb8c1edb3810196a3eff1c7a4188b2 |
| SHA1 | f117f6cbdc33cace7ee8026f8eebfc7a04a58a3c |
| SHA256 | 0477e8fa82354dc04fc44a23a05b069909aa5525f3ea474c2217a5a16a734aa2 |
VirusTotal upload shows the file is not signed but has a Product description of “Trend Micro AntiVirus Plus AntiSpyware”. It is categorized as part of the armadillo malware family.
slade.safehousenumber[.]com
9/94, https://www.virustotal.com/gui/domain/slade.safehousenumber.com
URLScan reaches the domain but produces a blank white page: https://urlscan.io/result/019567f0-6bd6-7669-976e-9da47cfe8b30/
44.221.84[.]105
1/94, https://www.virustotal.com/gui/ip-address/44.221.84.105
IP is AWS owned and serves many other domains — both legitimate and malicious.
URLScan also shows a blank page: https://urlscan.io/result/01956809-0a45-7eed-925f-fe6e637b1665/
portal.roomshowerbord[.]com
5/94, https://www.virustotal.com/gui/domain/portal.roomshowerbord.com
Known malware C2 domain.
193.166.255[.]171
2/94, https://www.virustotal.com/gui/ip-address/193.166.255.171
Large Finnish ISP that provides hundreds of resolutions.
URLScan shows the IP does not provide a web page: https://urlscan.io/result/01956a2a-e667-7bb8-9f13-23e97f7e4d0f/
Conclusion
Malware reaches out to C2 for second stage but these are no longer functioning — even though the domains are still alive.
IOCs
44.221.84[.]105
193.166.255[.]171
portal.roomshowerbord[.]com
slade.safehousenumber[.]com
0477e8fa82354dc04fc44a23a05b069909aa5525f3ea474c2217a5a16a734aa2