In November 2024, APT28, also known as Fancy Bear, executed a Wi-Fi breach using a technique dubbed the “Nearest Neighbor Attack.” This Russian state-sponsored group, tied to the GRU’s Unit 26165, compromised an organization’s network by exploiting a Wi-Fi connection from a nearby building. The incident was reported on X by @androidmalware2 on November 23, 2024, detailing how APT28 used a hacked laptop to infiltrate the target’s infrastructure.
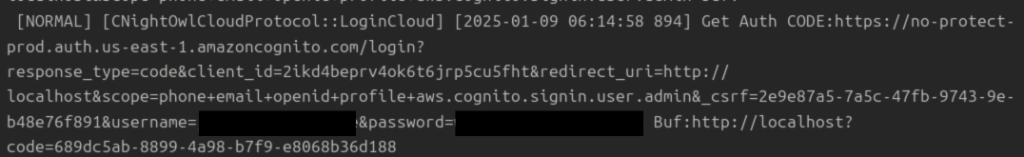
The attack began with APT28 gaining control of a laptop in a neighboring location, likely through phishing or a prior breach. Positioned within Wi-Fi range—typically 100-300 feet—they targeted the victim’s wireless network. The group employed credential stuffing, using stolen or brute-forced Wi-Fi passwords to connect. Once authenticated, they exploited weak network segmentation to access internal systems. The breach relied on physical proximity, bypassing external firewalls and VPNs that protect remote entry points.
The target was not publicly identified but fits APT28’s profile: government agencies, defense contractors, or critical infrastructure providers. The compromised network yielded sensitive data, potentially including operational plans or classified communications. APT28 masked their activity by routing traffic through the hacked laptop and additional proxies, complicating attribution. The attack’s success hinged on the target’s failure to secure Wi-Fi with strong encryption or monitor unauthorized connections.
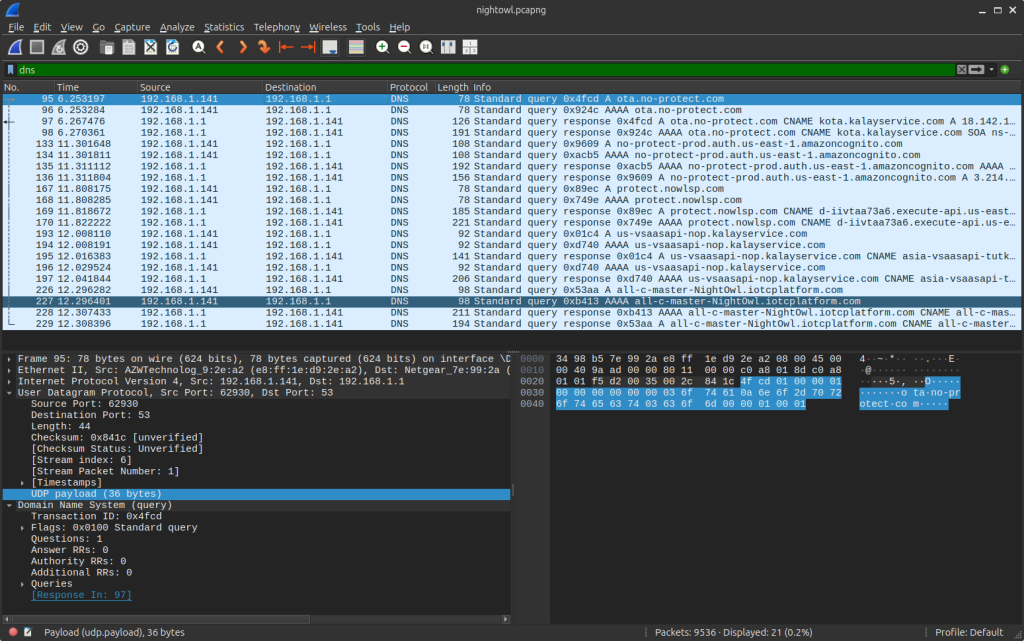
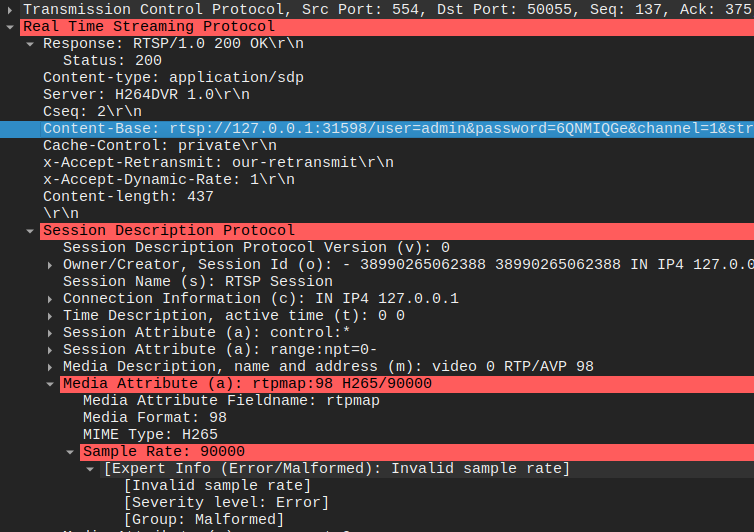
Technical details show APT28 used tools to sniff Wi-Fi traffic and crack WPA2/WPA3 credentials, possibly leveraging known vulnerabilities in router firmware. The breach exposed systems running outdated protocols or unpatched software, allowing lateral movement. Data exfiltration occurred over the Wi-Fi link, with the laptop acting as a bridge to external command-and-control servers. The incident’s late reporting—November 2024—suggests it occurred earlier in the year, with details surfacing after forensic analysis.
Mitigation requires securing Wi-Fi networks with WPA3 encryption, unique passwords, and MAC address filtering. Disabling unused wireless access points and monitoring for rogue devices can prevent similar attacks. Network segmentation limits damage post-breach, while endpoint detection tools flag suspicious activity. Physical security—ensuring Wi-Fi signals don’t leak beyond controlled areas—also matters. Organizations should audit nearby networks for compromised devices acting as entry points.
This attack aligns with APT28’s 2024 tactics, like their NTLM relay and phishing campaigns, but adds a physical twist. Their history—2016 DNC hack, 2017 NotPetya—shows a knack for blending cyber and real-world strategies. The Nearest Neighbor Attack exploited a rare but effective vector, proving not every breach needs a zero-day. If they can park a laptop next door, your fancy cloud defenses mean squat.
Fancy Bear’s basically your creepy neighbor with a Wi-Fi sniffer and too much time. The incident underscores APT28’s adaptability amid heightened scrutiny from U.S. and allied agencies. Recovery involved isolating the network, resetting credentials, and likely a lot of embarrassed IT meetings. Exact losses remain undisclosed, but downtime and data leaks were probable.
Next time, maybe invest in tinfoil for the office windows—stops Wi-Fi and alien probes. This breach highlights a low-tech vulnerability in a high-tech world. Organizations must lock down wireless access or risk APT28 turning their neighbor’s guest room into a hacking hub.