This is more or less a part five to the naprava.exe analysis. Turns out the SD card holds many malicious surprises.
Again, this is a 14-year-old malware executable from Moldova that was inadvertently stored on a SD card.
Analysis
Submitted the file to AnyRun. The file performs the following actions (with the respective timestamps):
| +47 ms | Loads C:\Users\admin\dosebe.exe |
| +63 ms | dosebe.exe writes a new shell key to WinLogon registry |
| +218 ms | Creates process svchost.exe |
| +703 ms | svchost.exe drops file C:\Users\admin\cbzvl.exe |
| +1517 ms | DNS request to jebena.ananikolic[.]su (45.144.3.149) |
| +32241 ms | DNS request to peer.pickeklosarske.ru (45.144.3.149) |
| +61963 ms | DNS request to teske.pornicarke[.]com (193.166.255.171) |
| +91680 ms | DNS request to juice.losmibracala[.]org (208.100.26.242) |
OSINT
| Filename | dosebe.exe |
| VirusTotal Score | 61/66 |
| MD5 | 40d00a6ddf83ba1641a45b1f804dbb1e |
| SHA1 | a15d491a472979b82c9c52b2c13310444d19cddb |
| SHA256 | a5de6732da831bda38e6ff36e47b826a572b609b1c98956832c8b19f5564087c |
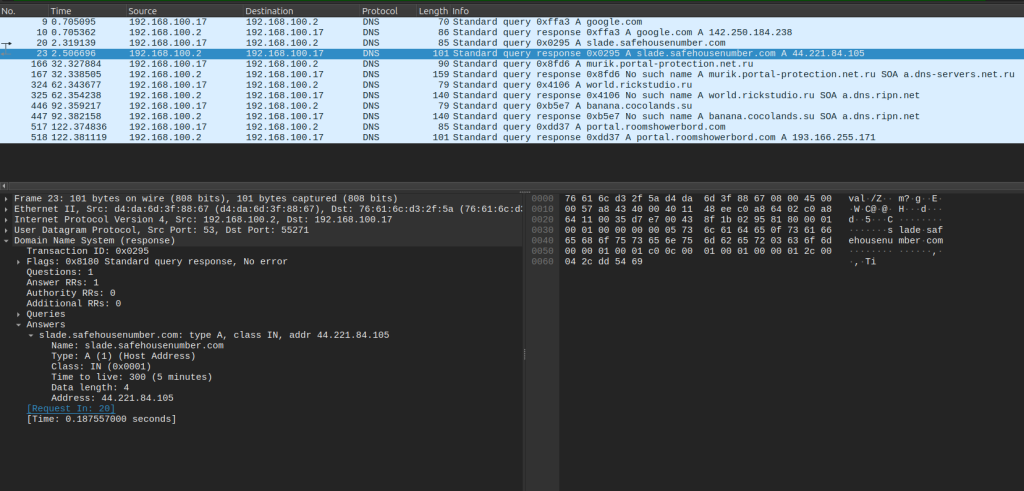
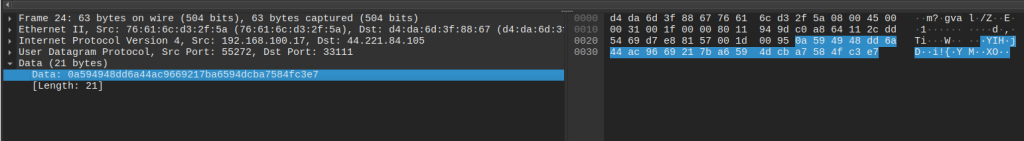
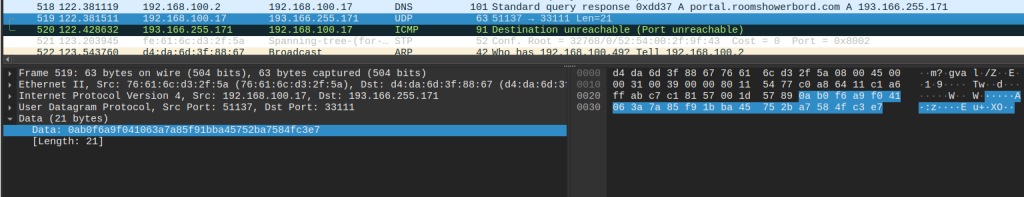
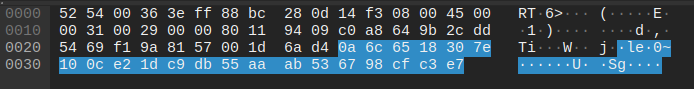
The executable drops the cbzvl.exe. This second executable writes a persistent reverse shell to the WinLogon registry. Then the original executable creates a svchost.exe process. The svchost.exe then runs the dropped file. This malware then reaches out to its C2 domains — slade.safehousenumber[.]com, portal.roomshowerbord[.]com, teske.pornicarke[.]com, and juice.losmibracala[.]org.
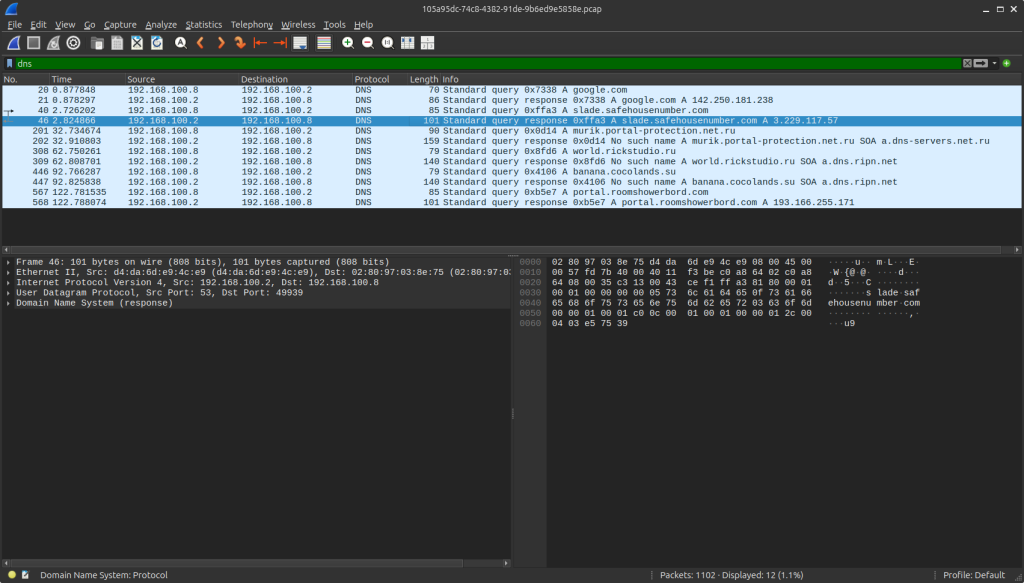
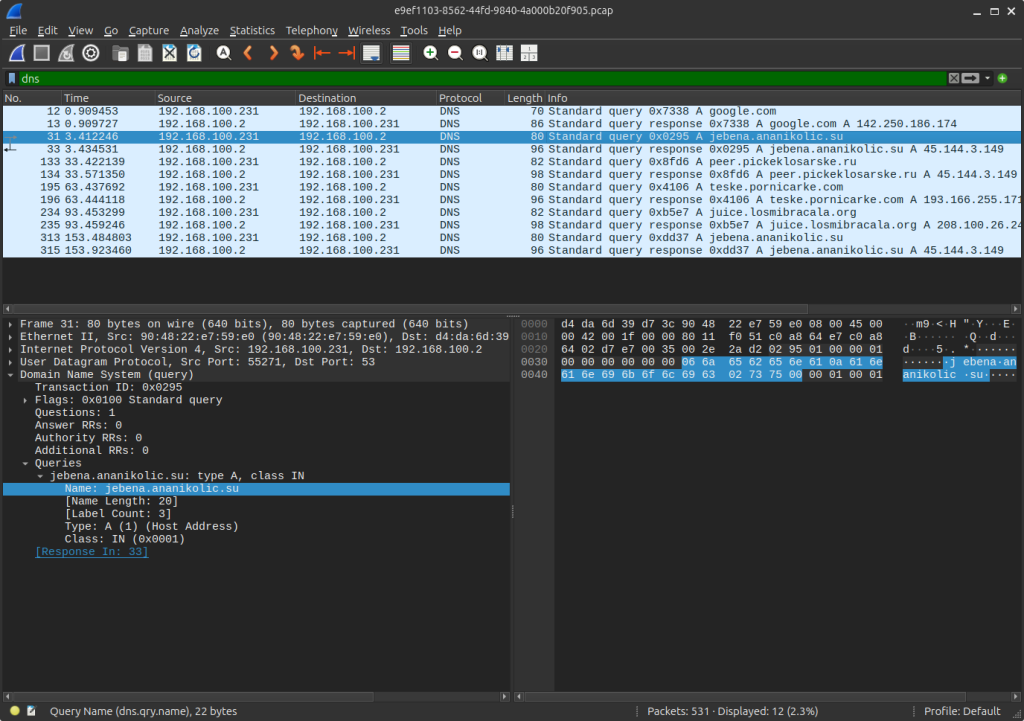
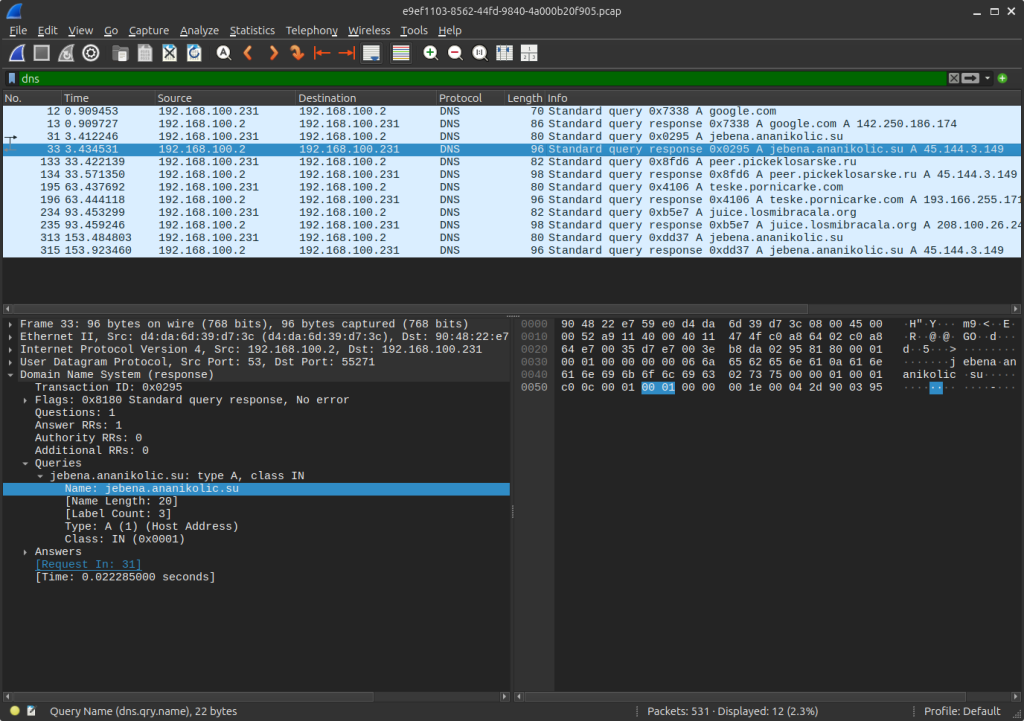
AnyRun captured a pcap and the DNS output is such:
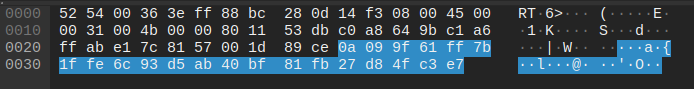
Request sent to jebena.ananikolic[.]su.
Response received:
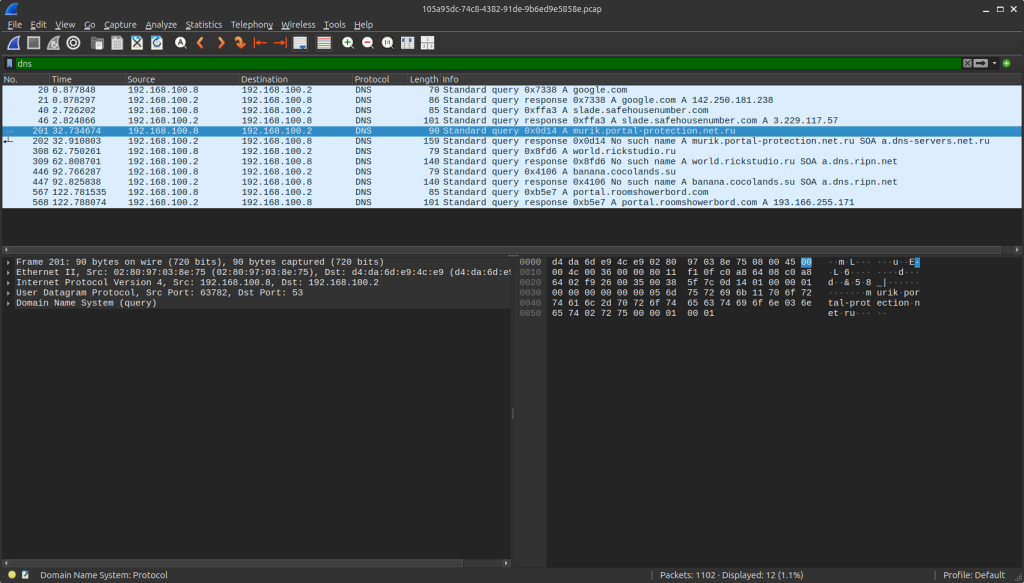
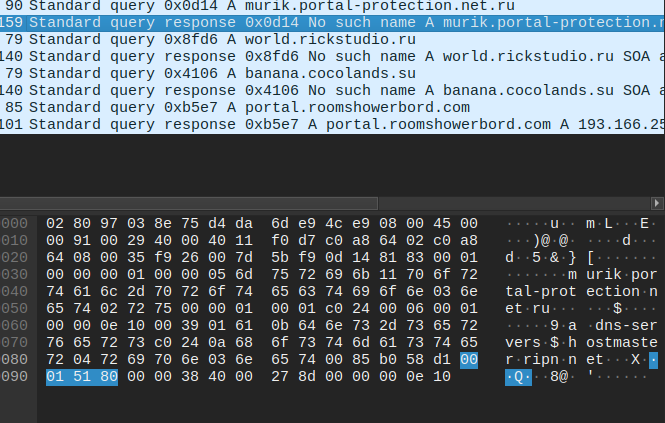
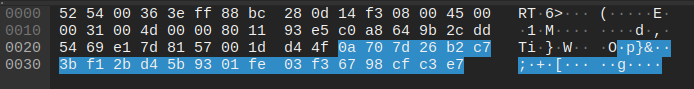
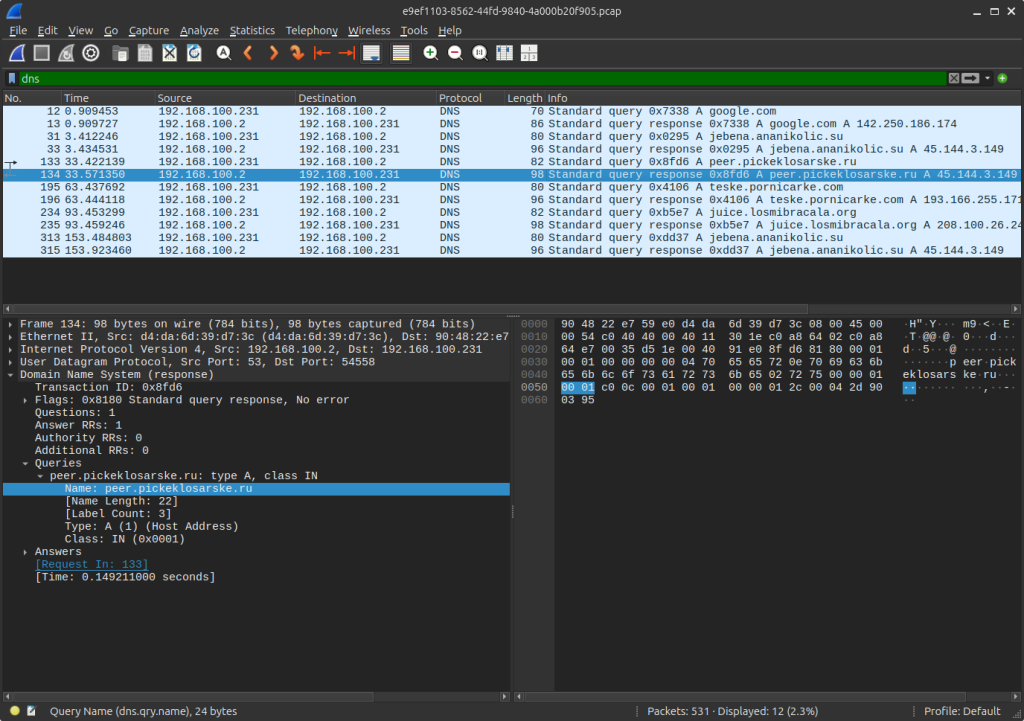
Request sent to peer.pickeklosarske[.]ru:
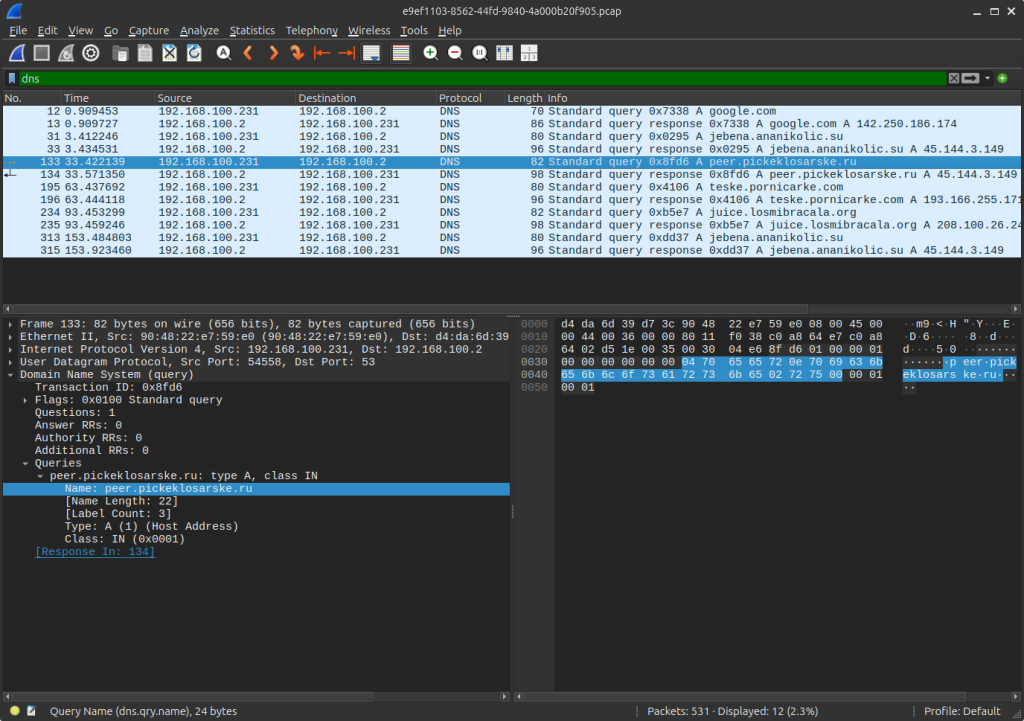
Response as:
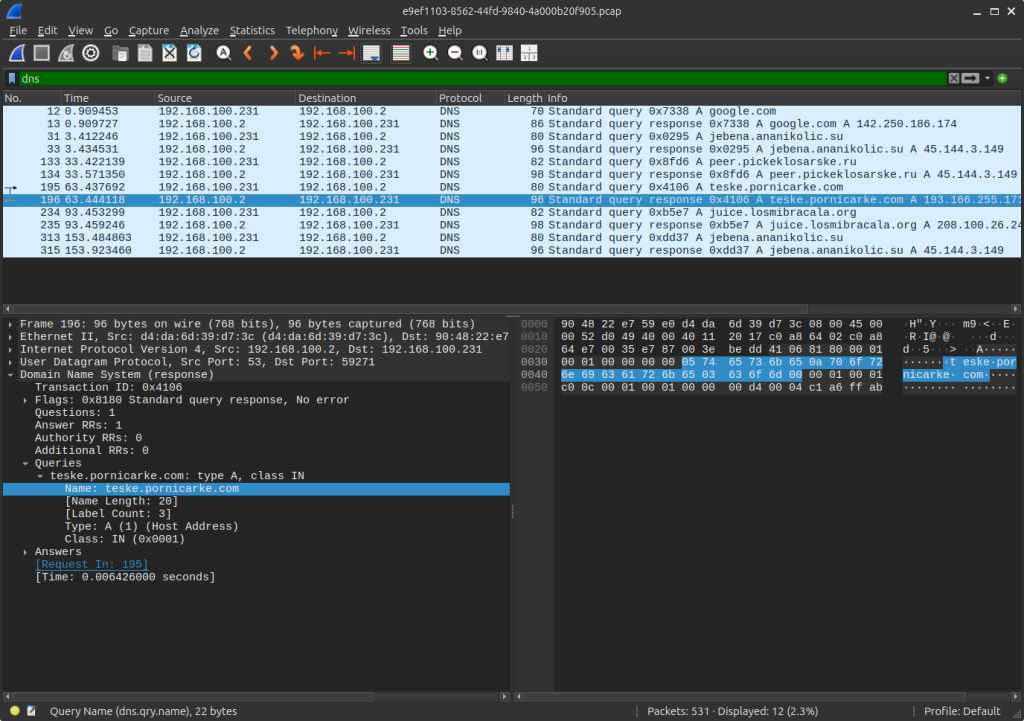
Request sent to teske.prnicarke[.]com:
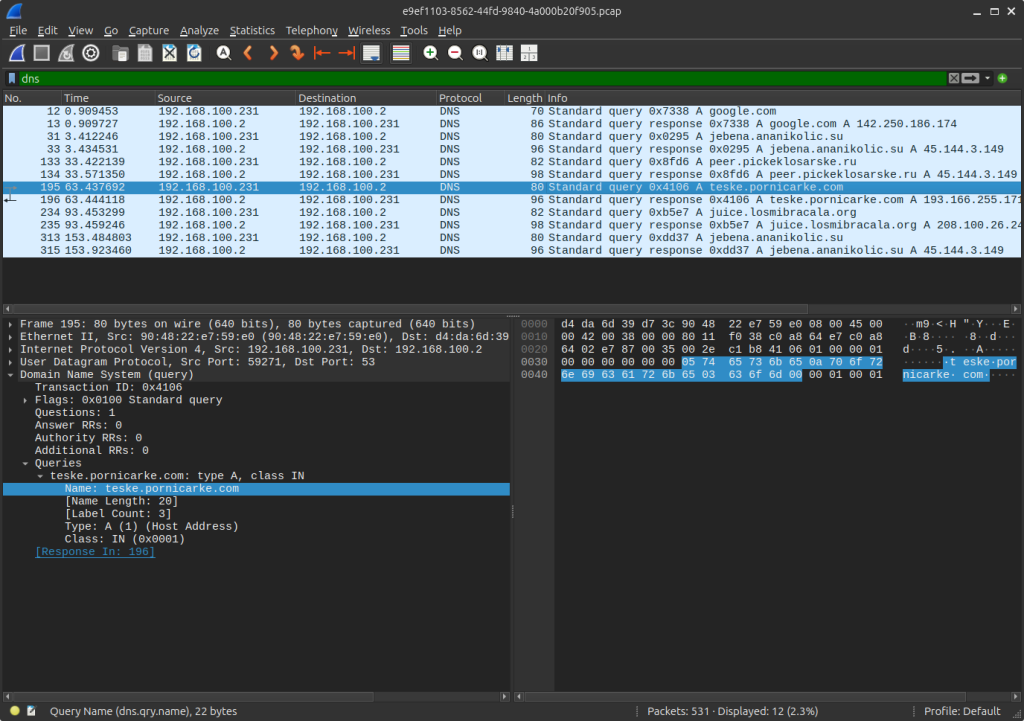
Response as:
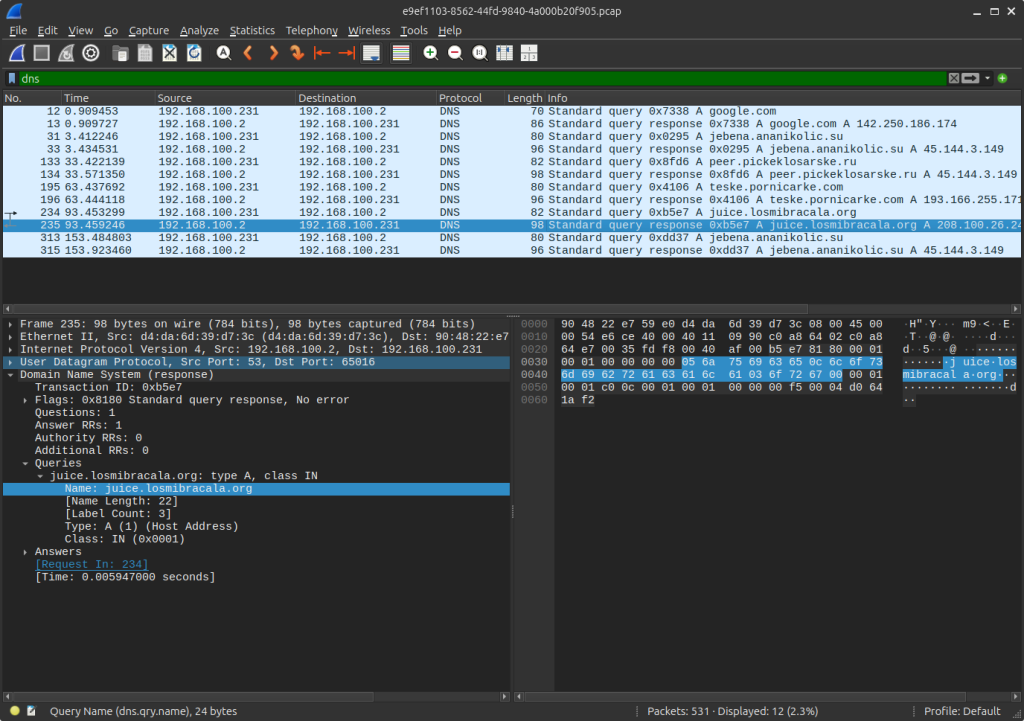
Request sent to juice.losmibracala[.]org:
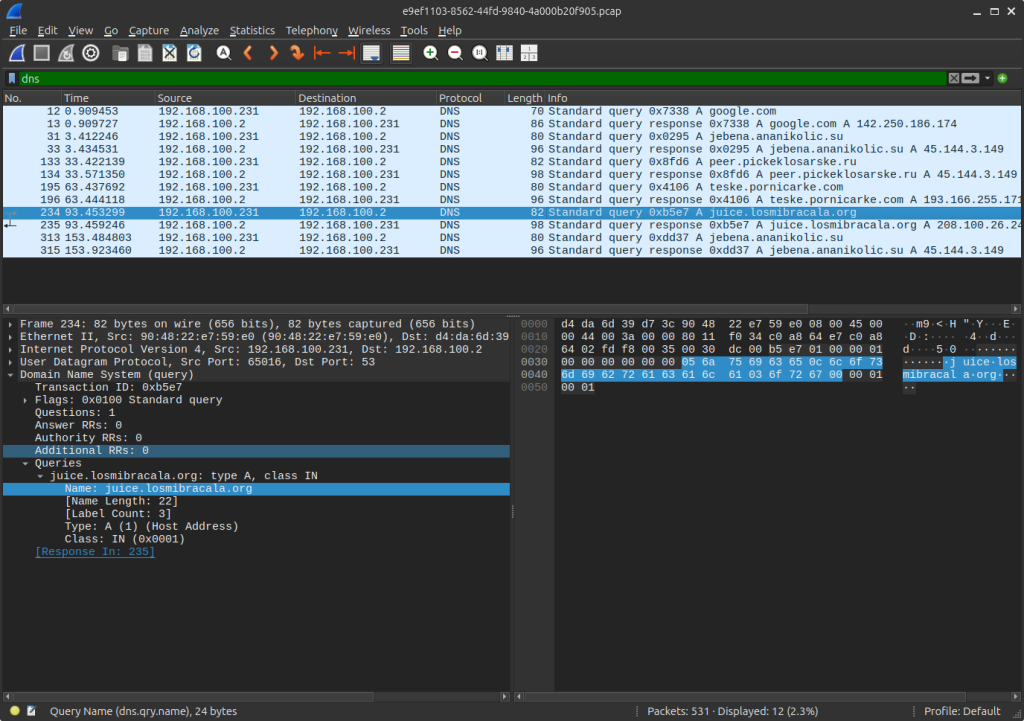
Response as:
Reverse engineering the malware with Ghidra gives the following decompilation:
void entry(void)
{
undefined4 uVar1;
undefined uVar2;
ushort in_AX;
UINT UVar3;
LPSYSTEMTIME p_Var4;
size_t sVar5;
int iVar6;
uint uVar7;
uint uVar8;
DWORD DVar9;
BOOL BVar10;
char extraout_CL;
char extraout_CL_00;
char extraout_CL_01;
char cVar11;
undefined extraout_CL_02;
byte extraout_CL_03;
uint extraout_ECX;
uint extraout_ECX_00;
uint extraout_ECX_01;
uint extraout_ECX_02;
uint extraout_ECX_03;
undefined4 extraout_ECX_04;
char *extraout_ECX_05;
char *extraout_ECX_06;
uint extraout_ECX_07;
short extraout_DX;
undefined2 extraout_DX_00;
short extraout_DX_01;
ushort extraout_DX_02;
short extraout_DX_03;
undefined2 extraout_DX_04;
int extraout_EDX;
char extraout_DH;
uint extraout_EDX_00;
uint extraout_EDX_01;
uint extraout_EDX_02;
uint extraout_EDX_03;
int extraout_EDX_04;
int extraout_EDX_05;
int extraout_EDX_06;
int extraout_EDX_07;
char extraout_DH_00;
uint extraout_EDX_08;
byte unaff_BL;
char *pcVar12;
char *unaff_ESI;
uint uVar13;
int iVar14;
ushort uVar15;
char *unaff_EDI;
bool bVar16;
byte bVar17;
short sVar18;
ushort uVar19;
char *pcVar20;
char *pcVar21;
char *pcVar22;
_STARTUPINFOA local_184;
_SYSTEMTIME local_140;
int local_12c;
_STARTUPINFOA local_128;
_STARTUPINFOA local_e4;
char *local_a0;
int local_9c;
ushort local_98;
undefined local_94;
uint local_90;
ushort local_8c;
char *local_88;
_STARTUPINFOA local_84;
char local_40;
byte local_3c;
LARGE_INTEGER local_38;
ushort local_30;
char *local_2c;
char *local_28;
_SYSTEMTIME local_24;
short local_14;
byte local_10;
char *local_c;
char *local_8;
if (((ushort)unaff_EDI & in_AX) != 0) {
strlen("Ycicst. Srybs C");
unaff_EDI = local_8;
}
bVar17 = (byte)local_c;
local_8 = (char *)0x0;
UVar3 = GetOEMCP();
if (DAT_0040a007 == extraout_CL) {
if ((UVar3 & 0xf409) == 0) {
local_8 = (char *)((int)local_8 - 0xb2ef8);
local_10 = unaff_BL & bVar17;
}
local_c = (char *)((int)local_c + 0x54da70);
local_14 = (short)unaff_EDI;
}
pcVar22 = local_8;
p_Var4 = &local_24;
GetSystemTime(p_Var4);
if (p_Var4 == (LPSYSTEMTIME)0x0) {
pcVar22 = (char *)CONCAT31((int3)((uint)pcVar22 >> 8),~(byte)pcVar22);
unaff_EDI = (char *)((uint)unaff_EDI & (uint)local_8);
p_Var4 = (LPSYSTEMTIME)0x0;
DAT_0040a108 = 0xa4;
_DAT_0040a0dc = 0;
}
_DAT_0040a10c = SUB42(p_Var4,0);
strlen("Mootnm Ipwru. Hkj");
DAT_0040a088 = 0xffffffff;
pcVar20 = "Fmsmhw Ji, Xim. C";
strlen("Fmsmhw Ji, Xim. C");
if (local_14 == (short)unaff_EDI) {
local_c = (char *)((int)local_c + 0x168);
}
local_8 = pcVar20;
puts("Tutqyud Silqx Bkcf");
local_14 = 0x2b0;
strlen("Tycah Itd, Eekq");
if (DAT_0040a109 != (byte)pcVar22) {
DAT_0040a110 = DAT_0040a110 - extraout_EDX;
}
local_c = (char *)((uint)local_c & 0x584320);
DAT_0040a08c = DAT_0040a08c + 0x1b87a4;
DAT_0040a007 = (char)((uint)extraout_EDX >> 8);
local_8 = pcVar22;
puts("Jwbcam. Iunei. N");
if (local_8 != unaff_ESI) {
local_28 = unaff_EDI;
local_14 = (short)unaff_EDI;
}
local_2c = (char *)0xa4;
local_c = (char *)((uint)local_c | 0xc17010);
local_30 = 0;
uVar7 = (int)unaff_EDI - (int)DAT_0040a090;
UVar3 = GetACP();
bVar16 = false;
if (UVar3 != 0) {
bVar16 = local_2c < unaff_ESI;
if (local_2c == unaff_ESI) {
bVar16 = 0xf99f < (ushort)UVar3;
}
local_30 = 0xffff;
}
local_28 = (char *)(((int)local_28 - 1U) - (uint)bVar16);
local_14 = 0xa010;
sVar5 = strlen("Ysviuic Wvocjk, T");
if ((DAT_0040a10a == (char)((uint)pcVar22 >> 8)) && (local_10 = 0x74, (sVar5 & 0x54d78432) != 0))
{
local_8 = (char *)0xffffffff;
}
QueryPerformanceCounter(&local_38);
pcVar22 = (char *)DAT_0040a088;
pcVar20 = local_c;
GetSystemTime((LPSYSTEMTIME)&DAT_0040a0e4);
if (pcVar20 != (char *)0x0) {
if ((char)pcVar20 != -0x1f) {
unaff_ESI = local_c;
}
DAT_0040a090 = (char *)0x0;
local_3c = extraout_CL_00;
}
if (pcVar20 == (char *)DAT_0040a104) {
strlen("Sybibl Jeiiklfh");
}
GetSystemTime(&local_24);
pcVar20 = "Fsbwlfq Eu, Fte";
sVar5 = strlen("Fsbwlfq Eu, Fte");
if (sVar5 == 0) {
local_14 = 0x360;
DAT_0040a012 = SUB42(pcVar22,0);
if (local_30 == 0x9e84) {
local_28 = (char *)((uint)local_28 | (uint)pcVar20);
}
DAT_0040a06c = 0;
}
uVar13 = (uint)unaff_ESI | sVar5;
puts("Mcho Cvtc Mhika Xi");
if (local_3c == (char)pcVar22) {
DAT_0040a024 = DAT_0040a024 - uVar7;
uVar13 = (uint)(char)pcVar22;
pcVar22 = (char *)DAT_0040a110;
}
local_28 = (char *)0x0;
GetSystemTime((LPSYSTEMTIME)&DAT_0040a114);
if (DAT_0040a124 != uVar13) {
if (extraout_ECX != uVar7) {
local_c = (char *)0x1;
}
local_30 = 1;
local_2c = (char *)uVar13;
}
local_40 = (char)pcVar22;
GetACP();
pcVar20 = local_8;
if (local_8 != (char *)extraout_ECX_00) {
if ((extraout_ECX_00 & uVar7) == 0) {
local_2c = (char *)0x1;
}
_DAT_0040a128 = _DAT_0040a128 ^ 0x3b4;
local_8 = (char *)0xffffffff;
pcVar22 = pcVar20;
}
DAT_0040a108 = DAT_0040a108 | (byte)(extraout_ECX_00 >> 8);
iVar6 = puts("Tbvt. Fkfnhf Bcdk");
DAT_0040a007 = (char)iVar6;
GetStartupInfoA(&local_84);
DAT_0040a007 = extraout_DH;
iVar6 = puts("Hgxhmlk Avfds Oaa");
FUN_004087d3();
if (((int)pcVar22 - iVar6 & extraout_ECX_01) == 0) {
p_Var4 = &local_24;
GetSystemTime(p_Var4);
if (p_Var4 == (LPSYSTEMTIME)0x0) {
local_8 = (char *)((uint)local_8 ^ extraout_EDX_00);
}
GetOEMCP();
}
sVar5 = strlen("Xilab Nduma Wlrgpen");
if (sVar5 != 0) {
local_8 = (char *)((uint)local_8 ^ 1);
}
UVar3 = GetACP();
DAT_0040a090 = (char *)((uint)DAT_0040a090 & extraout_EDX_01);
bVar16 = CARRY4((uint)local_2c,extraout_ECX_02);
uVar7 = (int)local_2c + extraout_ECX_02;
local_2c = (char *)(uVar7 + CARRY4(UVar3,(uint)local_28));
DAT_0040a104 = (DAT_0040a104 - 1) -
(uint)(bVar16 || CARRY4(uVar7,(uint)CARRY4(UVar3,(uint)local_28)));
local_88 = (char *)0xffffffff;
GetSystemTime(&local_24);
_DAT_0040a0e2 = _DAT_0040a0e2 - extraout_DX;
local_2c = (char *)0x0;
FUN_00407392();
DAT_0040a10b = DAT_0040a10b & 1;
GetStartupInfoA((LPSTARTUPINFOA)&DAT_0040a028);
pcVar22 = local_88;
cVar11 = 'h';
uVar7 = puts("Oobpuqc Fidhdlco");
if (uVar7 != 0) {
uVar7 = -uVar7;
}
DAT_0040a090 = pcVar22;
uVar13 = uVar7;
if (uVar7 == 0x4f225587) {
uVar13 = GetACP();
cVar11 = extraout_CL_01;
}
local_40 = (char)uVar13;
DAT_0040a130 = (DAT_0040a130 - cVar11) - (uVar7 < 0x4f225587);
bVar17 = 0xff5ae08f < local_c;
local_c = (char *)((int)local_c + 0xa51f70);
GetSystemTime(&local_24);
bVar16 = CARRY4(_DAT_0040a0f4,extraout_ECX_03);
uVar7 = _DAT_0040a0f4 + extraout_ECX_03;
_DAT_0040a0f4 = uVar7 + bVar17;
local_2c = (char *)(((int)local_2c + -0x3e7f8) - (uint)(bVar16 || CARRY4(uVar7,(uint)bVar17)));
uVar7 = extraout_EDX_02 & 0xff;
uVar13 = local_90 & DAT_0040a080;
GetTickCount();
local_10 = (byte)extraout_ECX_04;
local_90 = uVar13;
FUN_00408943(extraout_ECX_04,extraout_DX_00);
local_3c = 0;
local_94 = extraout_CL_02;
if ((POPCOUNT(uVar7 & uVar13) & 1U) == 0) {
GetSystemTime((LPSYSTEMTIME)&DAT_0040a13c);
local_3c = 0xff;
local_94 = 0x7c;
uVar8 = puts("Sxfogiabg Ott My. A");
if ((DAT_0040a007 != '\0') &&
(uVar7 = uVar7 | uVar8, DAT_0040a14c = uVar13, (uVar8 & 0x832bb7f) == 0)) {
pcVar22 = local_2c;
local_2c = local_2c + 0x29c;
}
}
pcVar20 = (char *)CONCAT22((short)(uVar13 >> 0x10),(short)(char)uVar7);
GetTickCount();
local_28 = extraout_ECX_05;
uVar2 = 0x90;
iVar6 = puts("Abiqyb. Hkh, Fmku");
local_94 = uVar2;
if (iVar6 == 0) {
DAT_0040a076 = -0x6870;
DAT_0040a150 = pcVar20;
local_2c = pcVar22;
}
uVar7 = CONCAT22((short)(uVar7 >> 0x10),local_98);
GetACP();
sVar18 = 0x16a4;
puts("Fggoct, Gsnr, Xg");
if (DAT_0040a076 == sVar18) {
uVar7 = extraout_EDX_03 & 0xff;
_DAT_0040a0e0 = 0x8c38;
}
pcVar12 = (char *)CONCAT31((int3)(uVar7 >> 8),(char)uVar7 - DAT_0040a007);
pcVar21 = "Jnq. Vauqb. Wyfnn";
iVar6 = puts("Jnq. Vauqb. Wyfnn");
if (iVar6 != 0) {
local_c = (char *)((int)local_c - 0x204);
DAT_0040a074 = 0x2dc;
local_88 = pcVar21;
}
iVar6 = puts("Rlpvnuv Mcctsy, Qo");
if (iVar6 != 0) {
pcVar20 = pcVar20 + 1;
_DAT_0040a154 = _DAT_0040a154 | 0xc9de0;
local_98 = (ushort)pcVar22;
}
pcVar21 = "Yjlfs. Xsptho Klvob";
strlen("Yjlfs. Xsptho Klvob");
FUN_00408943(pcVar21,~extraout_DX_02);
sVar18 = 0x16f4;
sVar5 = strlen("Gjvuqgvhw Tvkal");
if (local_28 == pcVar20) {
local_2c = (char *)0x1;
_DAT_0040a10e = _DAT_0040a10e + -1 + (ushort)(sVar18 != 0);
local_8 = (char *)sVar5;
if (extraout_DX_03 == (ushort)((ushort)pcVar22 - extraout_DX_01)) {
local_8c = 0xffff;
}
}
if ((char)(sVar5 >> 8) == local_40) {
GetSystemTime((LPSYSTEMTIME)&DAT_0040a13c);
}
sVar5 = strlen("Pspucxhd Ubjy Tdv");
if (DAT_0040a024 != sVar5) {
pcVar20 = (char *)CONCAT22((short)((uint)pcVar20 >> 0x10),0xffff);
local_14 = 0;
local_28 = (char *)((uint)local_28 ^ 1);
_DAT_0040a0e0 = extraout_DX_04;
}
DVar9 = GetTickCount();
uVar7 = local_90;
iVar6 = local_9c;
if (local_90 != DVar9) {
local_10 = 0xb0;
_DAT_0040a00c = _DAT_0040a00c ^ 0x3dd67c;
local_2c = (char *)0x165cc0;
local_88 = pcVar20;
}
pcVar22 = "Ccdi, Ttlvel Jibylh";
strlen("Ccdi, Ttlvel Jibylh");
local_a0 = pcVar22;
sVar5 = strlen("Vytudd Lughjrjm Rfl");
if (sVar5 == 0) {
bVar16 = uVar7 < DAT_0040a008;
uVar7 = uVar7 - DAT_0040a008;
local_9c = (local_9c + -0x197428) - (uint)bVar16;
local_3c = 0;
}
GetStartupInfoA(&local_e4);
_DAT_0040a158 = iVar6;
local_a0 = local_a0 + extraout_EDX_04;
sVar5 = strlen("Ysryovb. Bqprr Fo");
uVar15 = (ushort)uVar7;
if (sVar5 == 0) {
uVar15 = local_98;
}
DAT_0040a150 = (char *)extraout_EDX_05;
strlen("Adfmn, Lmlpd. Gyrgm");
if (local_8c != uVar15) {
local_a0 = (char *)((uint)local_a0 | (uint)pcVar12);
local_98 = 0x930;
_DAT_0040a15c = 0x55e0;
local_88 = (char *)((uint)local_88 ^ 0xffffffc8);
}
GetStartupInfoA(&local_128);
local_a0 = (char *)0xb57d00;
bVar17 = FUN_00407392();
local_2c = (char *)((uint)local_2c & 0x3709d0);
bVar16 = (DAT_0040a109 & bVar17) != 0;
pcVar22 = extraout_ECX_06;
iVar14 = extraout_EDX_06;
pcVar20 = pcVar12;
if (bVar16) {
pcVar22 = "Rtfloofwp Goduw";
puts("Rtfloofwp Goduw");
local_14 = 0x3c;
pcVar20 = pcVar12 + -1;
iVar14 = extraout_EDX_07;
}
iVar14 = (iVar6 - iVar14) - (uint)(bVar16 && pcVar12 == (char *)0x0);
uVar19 = 0x1778;
DAT_0040a100 = pcVar22;
iVar6 = puts("Utufodo Fiydogv Cb");
bVar17 = local_8c < uVar19;
if (local_8c != uVar19) {
bVar17 = false;
if ((iVar6 + (int)local_8 & 0x6af9U) != 0) {
pcVar20 = (char *)(int)extraout_DH_00;
}
local_28 = (char *)0xffffffff;
local_88 = pcVar20;
}
GetOEMCP();
uVar1 = DAT_0040a0f8;
local_2c = (char *)DAT_0040a0f8;
GetTickCount();
local_28 = local_28 + bVar17 + 0x218;
strlen("Cqxmxdfdiy, Blh");
if (local_30 != uVar15) {
_DAT_0040a158 = _DAT_0040a158 + 0x2c1d04;
iVar14 = 0;
local_28 = (char *)((uint)local_28 | 0x697dc);
}
pcVar20 = "Valioyx. Tqawb. Kvf";
pcVar22 = (char *)puts("Valioyx. Tqawb. Kvf");
if (local_3c == (byte)pcVar22) {
DAT_0040a076 = (DAT_0040a076 + 1) - (ushort)(local_3c < (byte)pcVar22);
local_30 = 0x134;
local_9c = 0;
if ((int)pcVar20 <= (int)pcVar22) {
iVar14 = iVar14 + DAT_0040a06c + (uint)(pcVar22 < pcVar20);
}
}
bVar17 = ~(byte)((uint)uVar1 >> 8);
GetTickCount();
bVar16 = DAT_0040a004 < bVar17;
DAT_0040a004 = DAT_0040a004 - bVar17;
uVar7 = (uint)bVar16;
bVar16 = CARRY4((uint)local_c,extraout_ECX_07);
uVar13 = (int)local_c + extraout_ECX_07;
local_c = (char *)(uVar13 + uVar7);
_DAT_0040a158 = (_DAT_0040a158 - iVar14) - (uint)(bVar16 || CARRY4(uVar13,uVar7));
local_9c = iVar14;
FUN_004087d3();
bVar17 = 0;
local_14 = 0x12f0;
strlen("Mhewyj Hi. Yejpask");
pcVar22 = local_c;
puts("Usnguq, Fb, Ebqq. M");
_DAT_0040a00c = _DAT_0040a00c + 1 + (uint)bVar17;
GetACP();
DVar9 = GetTickCount();
if ((DVar9 != 0x61) && (strlen("Mixujmbx Khjawk Lh"), DAT_0040a100 != pcVar22)) {
local_12c = local_12c + -1;
local_88 = (char *)0x90;
}
GetACP();
GetSystemTime(&local_24);
GetACP();
GetSystemTime(&local_140);
uVar1 = DAT_0040a160;
DAT_0040a131 = DAT_0040a131 + -0x10;
GetStartupInfoA(&local_184);
if (DAT_0040a080 == extraout_EDX_08) {
local_10 = (byte)uVar1;
}
_DAT_0040a15c = 1;
BVar10 = QueryPerformanceCounter((LARGE_INTEGER *)&DAT_0040a078);
bVar17 = DAT_0040a108 < extraout_CL_03;
if (DAT_0040a108 != extraout_CL_03) {
bVar17 = local_8 < 0x9b5850;
if (local_8 != (char *)0x9b5850) {
bVar17 = 0xd4bb < (ushort)BVar10;
}
DAT_0040a0f8 = 0xf0378;
}
GetTickCount();
DAT_0040a150 = (char *)(((int)DAT_0040a150 + 1) - (uint)bVar17);
local_10 = 0;
local_40 = 0;
FUN_0040784e();
/* WARNING: Subroutine does not return */
ExitProcess(0);
}
Below is a step-by-step analysis of what the provided decompiled executable (entry function) does, presented in bullet points in the order of execution. This appears to be a Windows application entry point with a mix of system calls, string operations, and arithmetic/logic manipulations. Note that many operations seem obfuscated or redundant, which might suggest intentional complexity or incomplete decompilation context.
- Initial condition check: If the bitwise AND of
unaff_EDI(an uninitialized pointer) andin_AX(a register value) is non-zero, compute the length of the string"Ycicst. Srybs C"usingstrlenand setunaff_EDItolocal_8(initially uninitialized). - Set initial values: Assign
local_8to0x0(null) and retrieve the OEM code page viaGetOEMCP(), storing it inUVar3. - OEMCP and condition adjustments: Compare
DAT_0040a007withextraout_CL(a leftover register value). If equal: - If
UVar3 & 0xf409is zero, adjustlocal_8by subtracting0xb2ef8and setlocal_10to the bitwise AND ofunaff_BLandbVar17. - Increment
local_cby0x54da70and setlocal_14to the lower 16 bits ofunaff_EDI. - Get system time: Call
GetSystemTime(&local_24)to retrieve the current system time intolocal_24. If the pointerp_Var4is null (which shouldn’t happen here), perform bitwise operations onpcVar22andunaff_EDI, setDAT_0040a108to0xa4, and reset_DAT_0040a0dcto 0. - Miscellaneous assignments: Set
_DAT_0040a10cto the lower 32 bits ofp_Var4, computestrlen("Mootnm Ipwru. Hkj"), and setDAT_0040a088to0xffffffff. - String operations: Compute
strlen("Fmsmhw Ji, Xim. C"). Iflocal_14equals the lower 16 bits ofunaff_EDI, incrementlocal_cby0x168. - Output and more adjustments: Set
local_8to"Fmsmhw Ji, Xim. C", output"Tutqyud Silqx Bkcf"viaputs, setlocal_14to0x2b0, and computestrlen("Tycah Itd, Eekq"). IfDAT_0040a109differs from the lower byte ofpcVar22, subtractextraout_EDXfromDAT_0040a110. - Bitwise and arithmetic: Update
local_cwith a mask (& 0x584320), incrementDAT_0040a08cby0x1b87a4, setDAT_0040a007to the second byte ofextraout_EDX, output"Jwbcam. Iunei. N"viaputs, and conditionally setlocal_28andlocal_14iflocal_8differs fromunaff_ESI. - Further initialization: Set
local_2cto0xa4, updatelocal_cwith a bitwise OR (| 0xc17010), resetlocal_30to 0, computeuVar7as the difference betweenunaff_EDIandDAT_0040a090, and retrieve the ANSI code page viaGetACP(). - Code page comparison: Based on
GetACP()result, setlocal_30to0xffffif non-zero and adjustlocal_28with a carry flag. Setlocal_14to0xa010. - String and performance counter: Compute
strlen("Ysviuic Wvocjk, T"). If conditions involvingDAT_0040a10aandsVar5are met, setlocal_8to0xffffffff. CallQueryPerformanceCounter(&local_38)to get a high-resolution timestamp. - System time and conditions: Retrieve system time into
DAT_0040a0e4. IfpcVar20(previouslylocal_c) is non-null and not-0x1f, setunaff_ESItolocal_c. ResetDAT_0040a090to 0 and updatelocal_3c. IfpcVar20equalsDAT_0040a104, computestrlen("Sybibl Jeiiklfh"). - Repeated system time and string checks: Call
GetSystemTime(&local_24), computestrlen("Fsbwlfq Eu, Fte"). If the length is 0, setlocal_14to0x360, updateDAT_0040a012, and conditionally modifylocal_28andDAT_0040a06c. - Output and bitwise updates: Output
"Mcho Cvtc Mhika Xi"viaputs. Iflocal_3cequals the lower byte ofpcVar22, adjustDAT_0040a024and updateuVar13. Resetlocal_28to 0 and retrieve system time intoDAT_0040a114. - Conditional arithmetic: Based on comparisons involving
DAT_0040a124,extraout_ECX, anduVar7, updatelocal_c,local_30, andlocal_2c. Retrieve the ANSI code page again viaGetACP(). - More output and bitwise ops: If
local_8differs fromextraout_ECX_00, adjustlocal_2c,_DAT_0040a128, andlocal_8. UpdateDAT_0040a108and output"Tbvt. Fkfnhf Bcdk"viaputs. SetDAT_0040a007to the return value ofputs. - Startup info and function calls: Retrieve startup info into
local_84viaGetStartupInfoA, updateDAT_0040a007, output"Hgxhmlk Avfds Oaa", and callFUN_004087d3. Conditionally retrieve system time and adjustlocal_8. - String length and ACP: Compute
strlen("Xilab Nduma Wlrgpen"). If non-zero, XORlocal_8with 1. Retrieve the ANSI code page again and perform arithmetic onDAT_0040a090,local_2c, andDAT_0040a104. - More system calls and output: Set
local_88to0xffffffff, retrieve system time, adjust_DAT_0040a0e2, resetlocal_2c, callFUN_00407392, updateDAT_0040a10b, retrieve startup info intoDAT_0040a028, and output"Oobpuqc Fidhdlco". - Tick count and adjustments: Negate
uVar7if non-zero, updateDAT_0040a090, and conditionally retrieveGetACP()ifuVar7equals0x4f225587. AdjustDAT_0040a130andlocal_c. - Performance counter and system time: Retrieve system time, perform arithmetic on
_DAT_0040a0f4andlocal_2c, callGetTickCount(), and invokeFUN_00408943. Conditionally retrieve system time and output"Sxfogiabg Ott My. A". - Further string outputs: Output
"Abiqyb. Hkh, Fmku". If the return value is 0, updateDAT_0040a076andDAT_0040a150. RetrieveGetACP(), output"Fggoct, Gsnr, Xg", and conditionally update_DAT_0040a0e0. - String and pointer manipulations: Output
"Jnq. Vauqb. Wyfnn"and"Rlpvnuv Mcctsy, Qo", adjustinglocal_c,DAT_0040a074,_DAT_0040a154, andlocal_98based on return values. - Final system calls and exit: Repeatedly call
GetSystemTime,GetACP,GetTickCount, andGetStartupInfoA. Update various global variables (_DAT_0040a158,_DAT_0040a15c, etc.), callQueryPerformanceCounter, and invokeFUN_0040784e. Finally, terminate the process withExitProcess(0), which does not return.
Conclusion
Malware reaches out to C2 for second stage but these are no longer functioning — even though the domains are still alive.
IOCs
44.221.84[.]105
193.166.255[.]171
portal.roomshowerbord[.]com
slade.safehousenumber[.]com
world.rickstudio[.]ru
banana.cocolands[.]su
40D00A6DDF83BA1641A45B1F804DBB1E
A15D491A472979B82C9C52B2C13310444D19CDDB
A5DE6732DA831BDA38E6FF36E47B826A572B609B1C98956832C8B19F5564087C
dosebe.exe