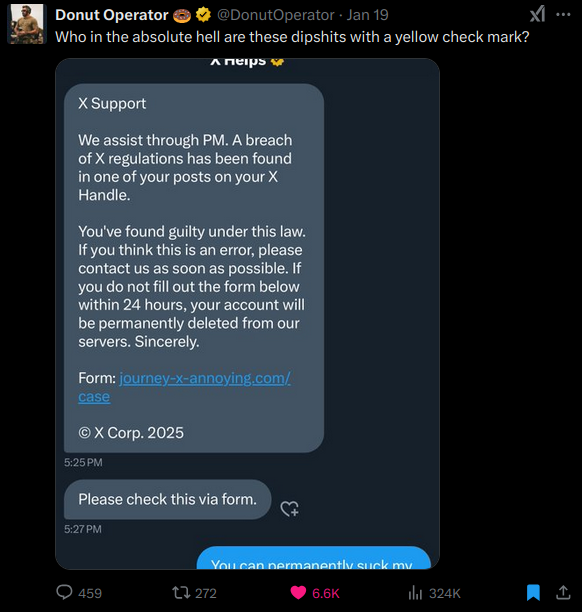
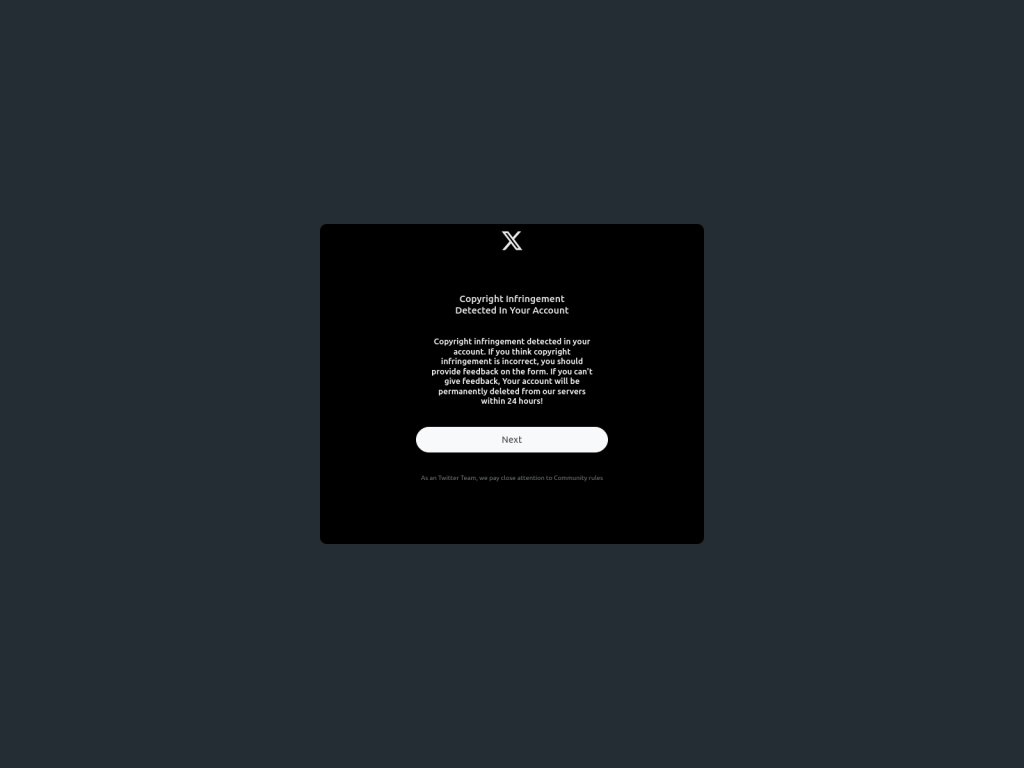
The University’s IT team reported the breach this month. The final object of the hackers’ actions: student and faculty data found in Office 365 and an Isilion database of documents. However, no public statement yet as to who did it or really why. I feel like it could’ve been a disgruntled student aiming to get info on another student or even teacher. But let’s look at basic issues that probably plague most public universities.
Office 365 MFA
Since 2019, Microsoft has been rolling out Security Defaults for individual and enterprise 365 solutions. Security Defaults include pre-enabled MFA setting for all users in the new tenant when it is set up.
This is great news for anyone signing up for a random personal Office 365 subscription or for a brand new business starting out. However, it is safe to say that most universities have been around a lot longer than 5 years.
This means MFA was most likely not enabled by default for Western Sydney University students and faculty. Even though it is possible that their IT team could have implemented MFA, I don’t see this security measure (no matter how important) to be the number one priority for a school. The IT department is probably swamped with provisioning new devices for new students each year and replacing broken tech as the year goes on.
Thus, in this hack the most probably and simple breach of entry was a set of compromised credentials or weak passwords — since university email address patterns are public knowledge, making it easy to guess usernames.
Isilon Storage
Isilon may sound like a fancy cloud solution but it is nothing more than a NAS device. It operates in a storage cluster using FreeBSD. This means it provides access via the HTTP, SMB, NFS, and FTP protocols.
And as any good script kiddie will do (such as myself), one will search and find the default admin credentials for Isilon devices. Turns it out it is root:a. That’s it. root for the username and a for the password.
Now I’m really hoping the storage admins did not keep this default credential set. But, even if it was changed, Isilon provides LDAP/AD authentication. So, if the hacker already breached 365 with working credentials, he could have easily accessed the file storage, as well.
Solutions
The answers are always simple. And in this case, it is no different.
Enable MFA and change default credentials. Yes, it will be annoying and cumbersome to set it up for hundreds or thousands of students and faculty, but it will save you your job later on. School systems are great places for SSNs, financial account numbers, passports, immigration documents, and even PHI. Nobody wants to deal with that mess.
To enable security defaults:
- Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
- Browse to Identity > Overview > Properties.
- Select Manage security defaults.
- Set Security defaults to Enabled.
- Select Save.
Lastly, change your NFS/SMB shares’ default credentials. Also, remember that if you do use LDAP/AD for authentication to the share, you may lose out on MFA tokens. I don’t know how Isilon, so that’s always a concern.