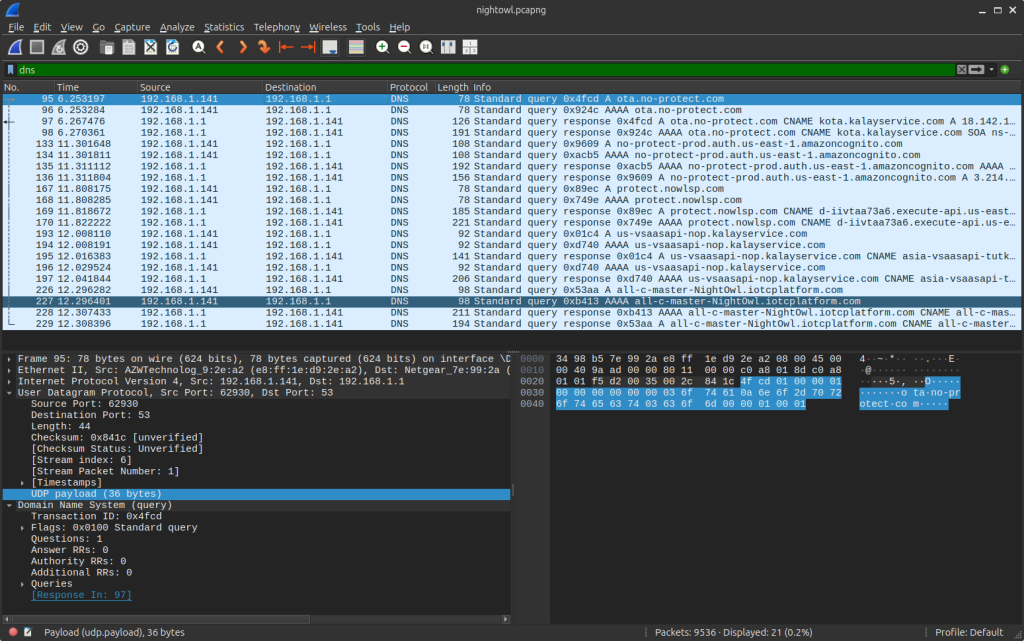
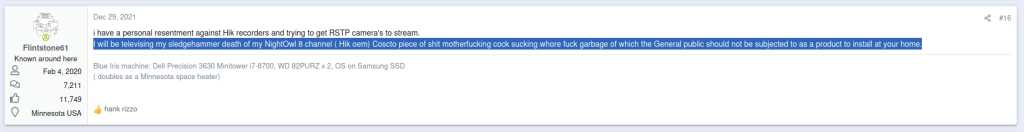
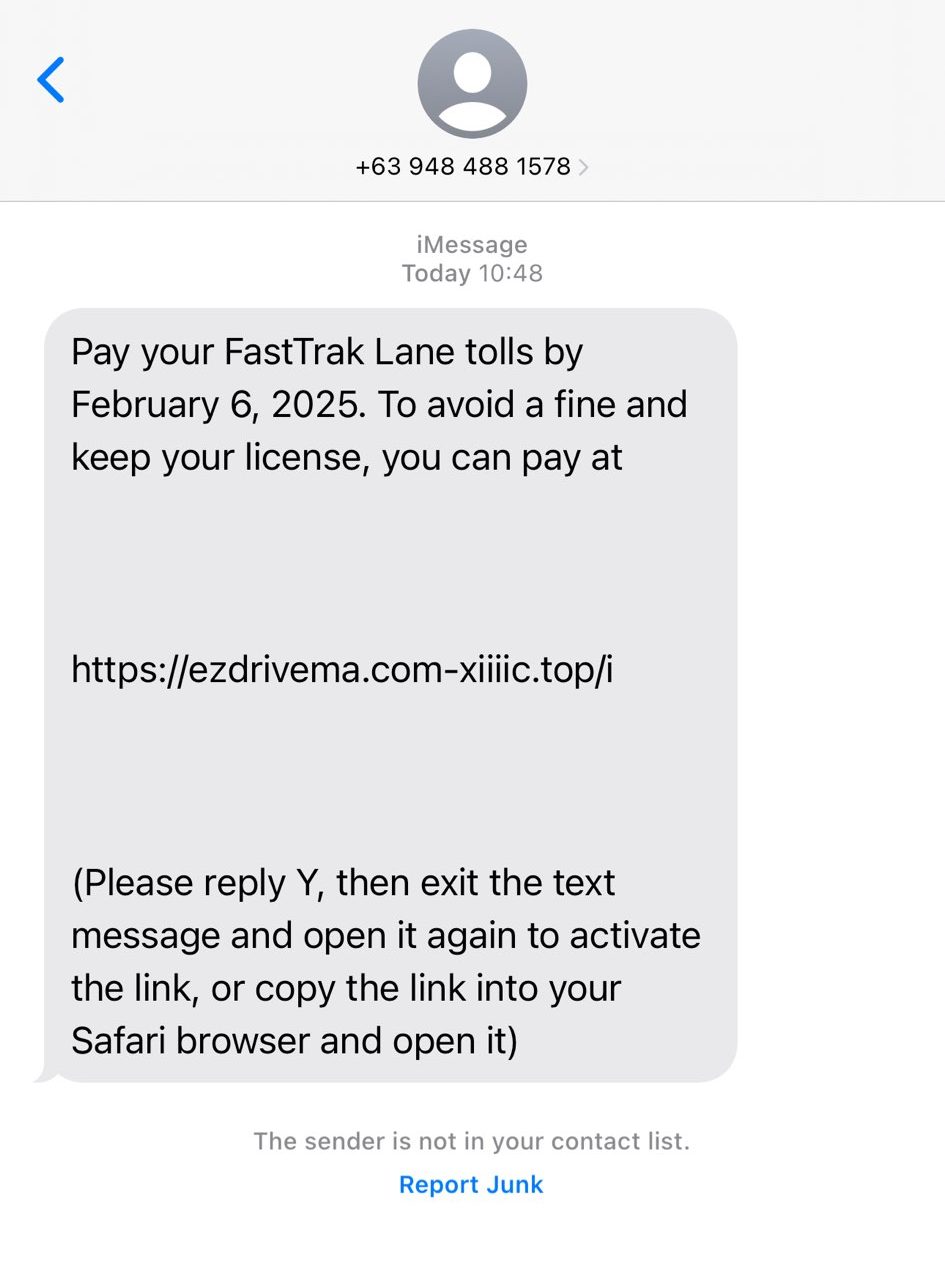
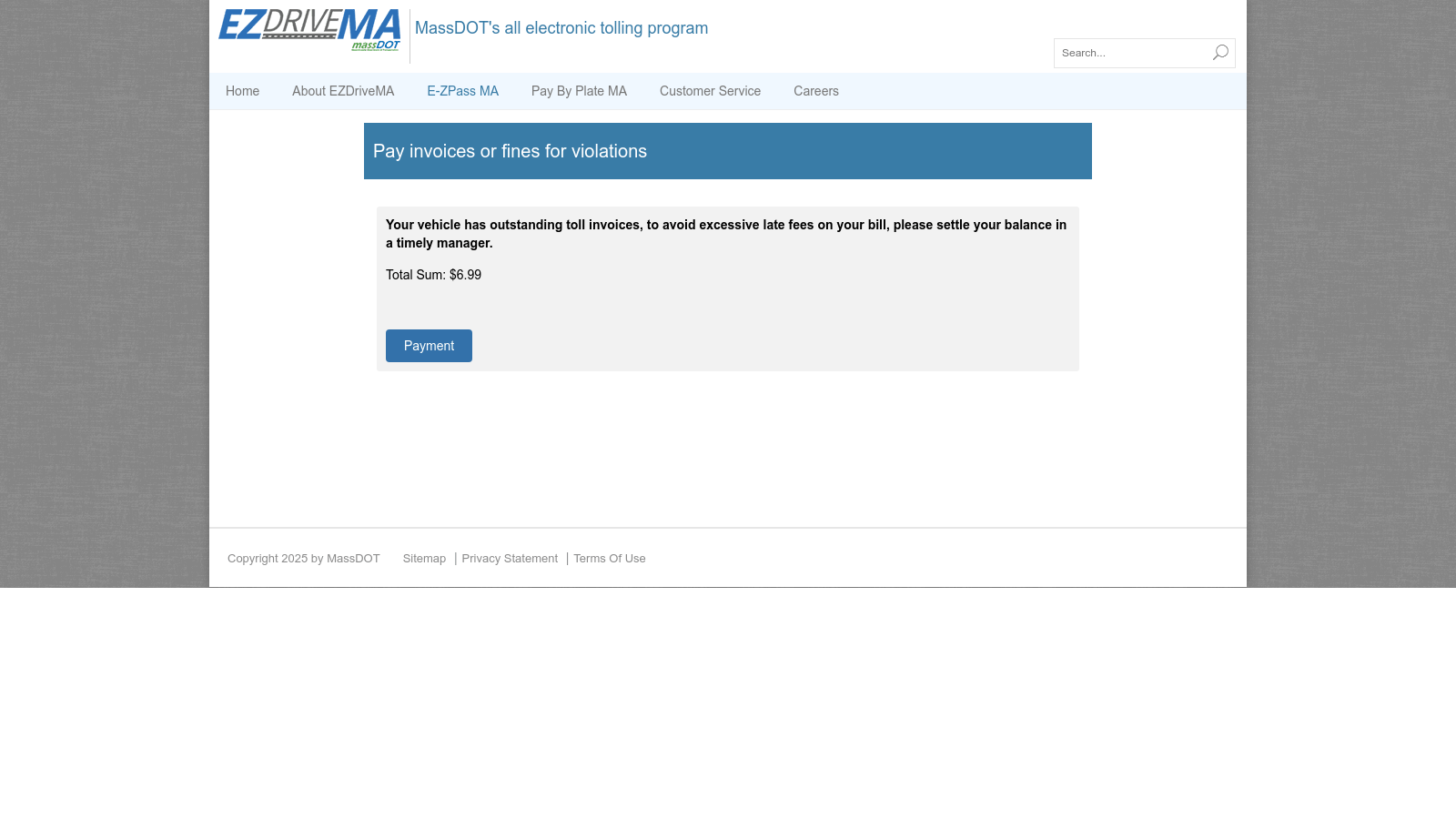
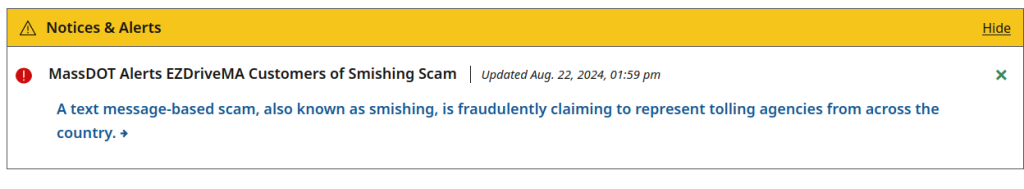
Analyzing the network traffic pcap led me to see that this “American” company is using a foreign (Taiwanese) P2P network and authentication infrastructure for viewing Night Owl streams via their CMS app. I don’t like it. However, it network traffic didn’t tell me why I can’t view live/recorded video playback in the Windows application. So, this requires a deepdive into the application logs. I also want to understand how the executable works and want to learn how to use Ghidra/reverse engineer more in depth.
Application Logs
I copied the program parent directory over to my linux machine for analysis. Navigated to ..\OprLog and found the app log files. During inspection of an entire log file, I found no errors regarding video playback. But, interestingly enough, Night Owl stores credentials in plaintext!!!
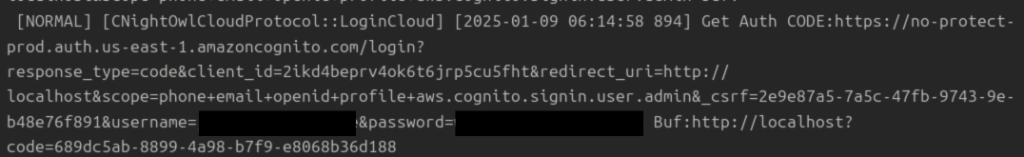
It’s 2024, people. Can we not store creds in plaintext, please??
But, alas, since I still did not find any ERROR messages regarding playback, it is time to dig into reverse engineering the firmware.
Ghidra
My DVR version is DVR-FTD4-8. I downloaded the firmware file from here: https://support.nightowlsp.com/hc/en-us/articles/13090197774747-FTD4-Series
Next, I attempted to import the firmware bin into Ghidra, but found that I did not know the architecture. I could make an educated guess, but really had no idea what DVR systems use for processors.
So, I attempted attach a keyboard to the device, reboot the DVR, and spam any and all the keys that would result in accessing the bootloader in order to find the specific processor architecture. But no such luck occurred.
I ended up pulling the plug on the DVR and opening up the case.


Unfortunately, the processor is covered with the heat sink. Next best thing is to look up the board schematics to see if there are correlating FCC documents showing specific processors. Motherboard is AHB8008T-NB-T36-OWL v1.02.

I found an FCC document for the bluetooth chip radiation evaluation. However, this does not provide any schematics or information on the processor.
There is no information on this specific OWL-branded board, so I queried for only AHB8008T and found that there are various security camera DVRs using this parent board. This resulted in me finding a CVE referencing this board and its manufacturer, that the manufacturer Xiongmai.
I searched for Xiongmai plus the board name and found that it uses a Hisilicon Hi3531D:
The above documentation explains that this processor uses ARM Cortex A9@1.4 GHz. I imported it as ARM Cortex (little endian).
Conclusion of Part One
I now have the firmware loaded into Ghidra. I also already have the exe and all dlls ready for import. Does the firmware contain any helpful information for me to find out why I’m experiencing the black video playback? Probably not. But I want experience in reverse engineering firmware.
Most likely the video playback error will be found in a dll and referenced in the exe. But I am also interested in finding security vulnerabilities in this product (such as the plaintext credentials) since I use this to help secure my home. And I’m also interested in finding how much of what is being sent to foreign companies and governments (and possible adversaries). Then I want to find these devices on shodan to see if I can exploit their p2p protocol.